Medusa Ransomware detection
Introduction
Medusa is RansomWare that will run specific tasks to prepare the target system for the encryption of files, Medusa was first seen in 2019, Medusa avoids executable files, probably to avoid rendering the targeted system unusable for paying the ransom, Medusa Locker has been known to exploit Remote Desktop Protocol (RDP) vulnerabilities to gain access to a victim’s machine, It uses a combination of AES and RSA-2048, and reportedly appends extensions such as .encrypted, .bomber, .boroff, .breakingbad, .locker16, .newlock, .nlocker, and .skynet.
How To Do it
I will use IDA Pro as my tool to help me with this project, first one of the most things that identify a sample or a family of Malware is Strings, looking at strings gives us a lot of options to include in our yara rule
strings
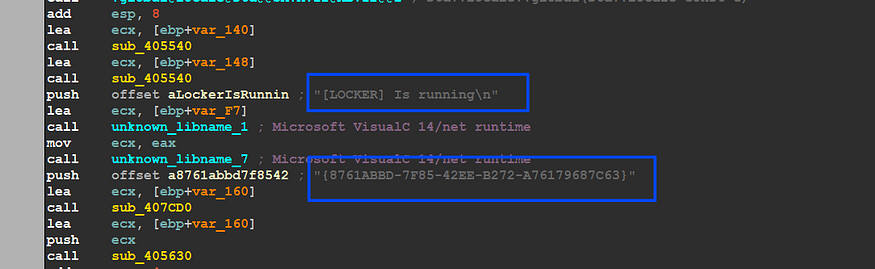
the malware uses a removed PrintF in C++, the second string is a string, so we need to take a look at all strings we get some useful ones
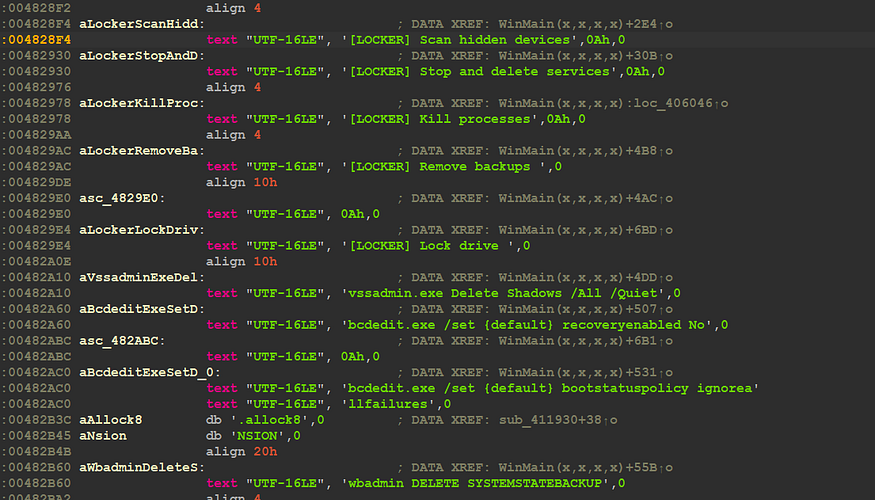
“ {8761ABBD-7F85–42EE-B272-A76179687C63} ”
“ [LOCKER] Is running ”
“ vssadmin.exe Delete Shadows /All /Quiet ”
“ bcdedit.exe /set {default} recoveryenabled No”
‘ wbadmin DELETE SYSTEMSTATEBACKUP -deleteOldest ’
and I have another sample that is 64 bit, I need to explore it
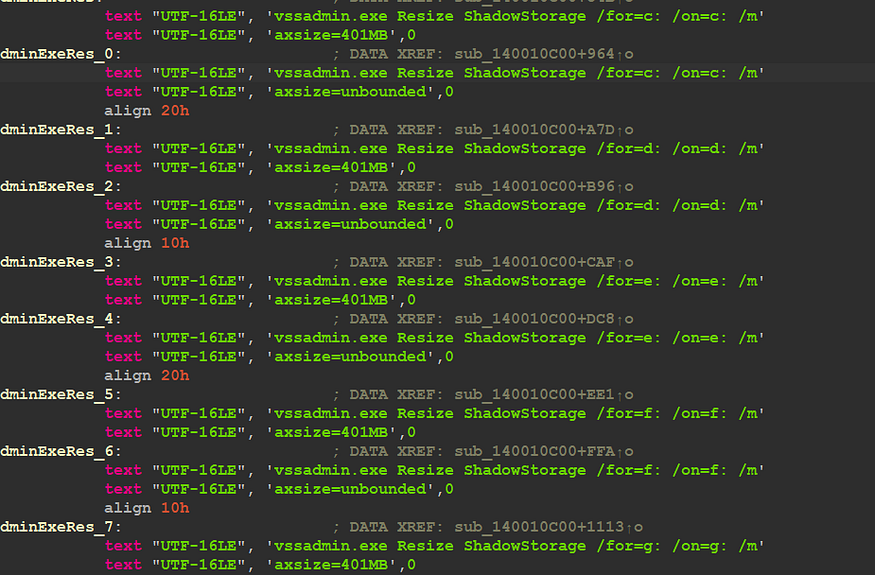
64-bit strings
“vssadmin.exe Delete Shadows /All /Quiet”
“bcdedit.exe /set {default} recoveryenabled No”
“wbadmin DELETE SYSTEMSTATEBACKUP”
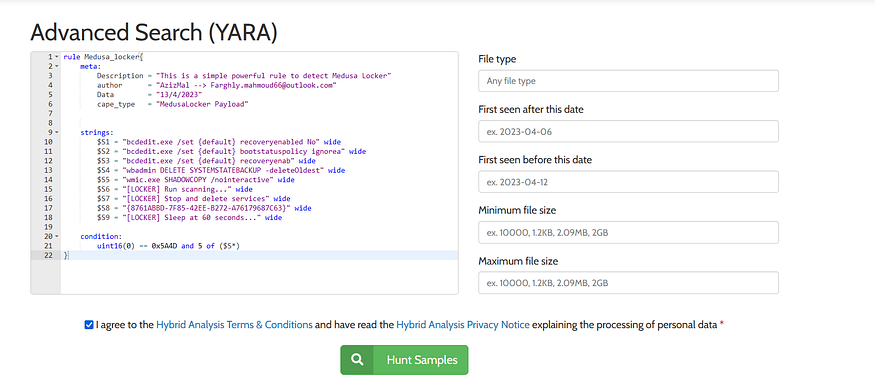
so let’s build our rule to detect this family
rule Medusa_locker{
meta:
Description = "This is a simple powerful rule to detect Medusa Locker"
author = "AzizMal --> Farghly.mahmoud66@outlook.com"
Data = "13/4/2023"
cape_type = "MedusaLocker Payload"
strings:
$S1 = "bcdedit.exe /set {default} recoveryenabled No" wide
$S2 = "bcdedit.exe /set {default} bootstatuspolicy ignorea" wide
$S3 = "bcdedit.exe /set {default} recoveryenab" wide
$S4 = "wbadmin DELETE SYSTEMSTATEBACKUP -deleteOldest" wide
$S5 = "wmic.exe SHADOWCOPY /nointeractive" wide
$S6 = "[LOCKER] Run scanning..." wide
$S7 = "[LOCKER] Stop and delete services" wide
$S8 = "{8761ABBD-7F85-42EE-B272-A76179687C63}" wide
$S9 = "[LOCKER] Sleep at 60 seconds..." wide
condition:
uint16(0) == 0x5A4D and 5 of ($S*)
}
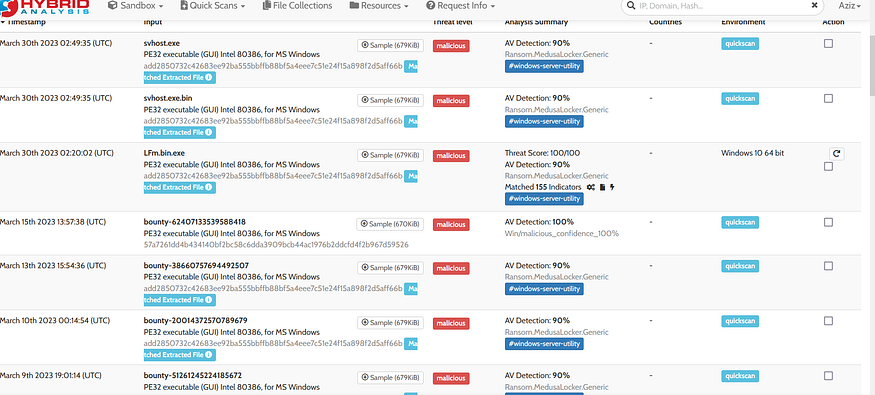
I have 4 samples and I will test them, then I will use an online sandbox to scan a wide range of samples , and here is the result bro
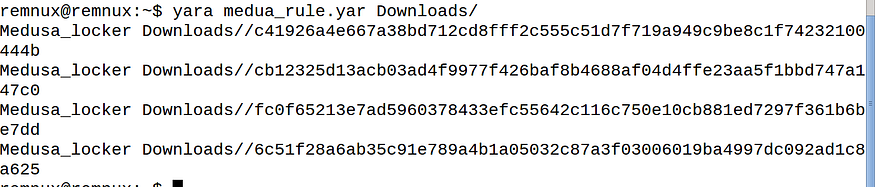
local scanning
using hybrid-analysis.com we got awsom results
more detection (60 sample) in the sandbox give us how the yara is good, and here is the link if u want to check click here
thanks for reading -_-
thanks for MalGamy
follow me
