Death RansomWare part_2
Introduction
Hello Geeks, in Part_1 we talked about the unpacking process of Ransomware and in this Article, I will complete the analysis and extract how the encryption methodology is done and what files are being encrypted, in the end, I will write a simple Yara rule to detect this Variant of Death Ransom, so let’s dig into the analysis process
Basic Static :
the malware looks straightforward with low entropy, and that means it will not do decryption of its configuration
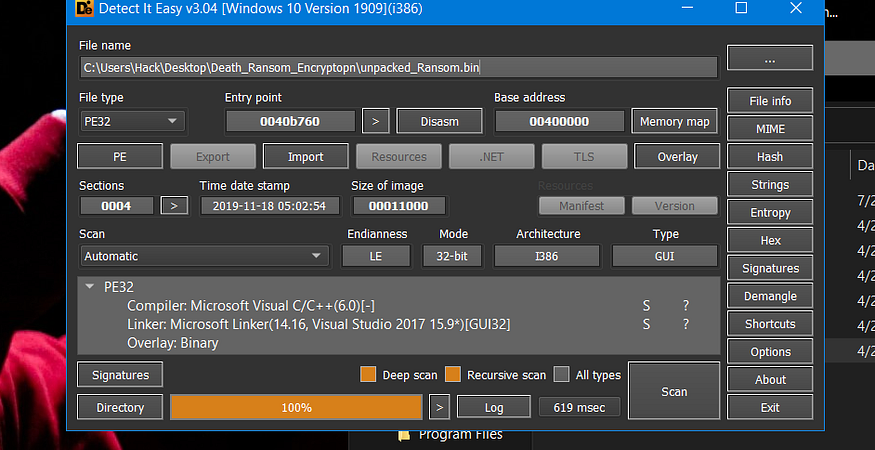
so let’s take a look at its strings, which give us strings like (Ransomware messages and some things related to shadow copy, etc….)
Avoid Infection :
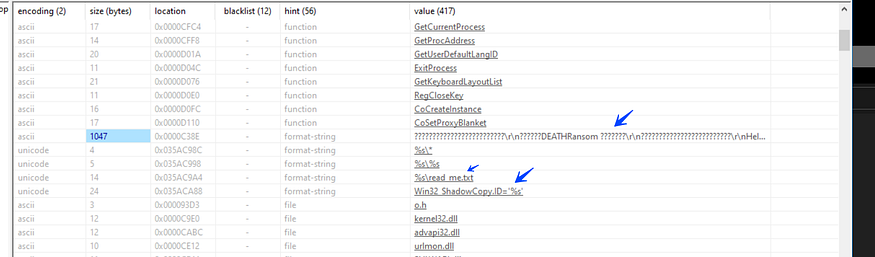
the malware starts its behavior by avoiding infection for some countries using these APIs
to retrieve the machine languages and keyboard-installed languages, and here is the malware to avoid infecting users of some Asian Countries like
1049 → Russian language
1087 → Farsi (Persian) language
1059 → Belarusian language
1058 → Ukrainian language
1092 → Azerbaijani language
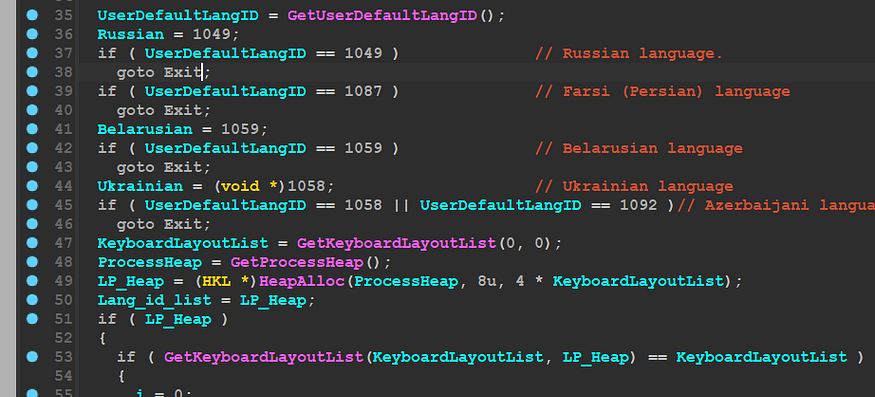
Getting MachineIP :
the sample then tries to connect to “HTTP://iplogger[.]org/1Zqq77 “ and download a File Called “ntos.database” using URLDownloadToFilA() API
and if we try to open the downloaded file, it’s an HTML File
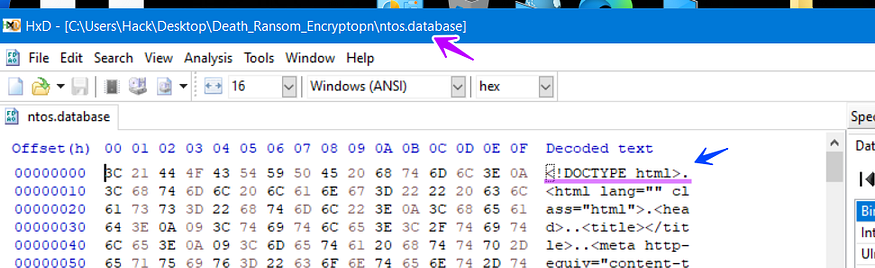
so let’s try to open it in the browser to check its content all of this connection is some noise only but can be used as IOCs
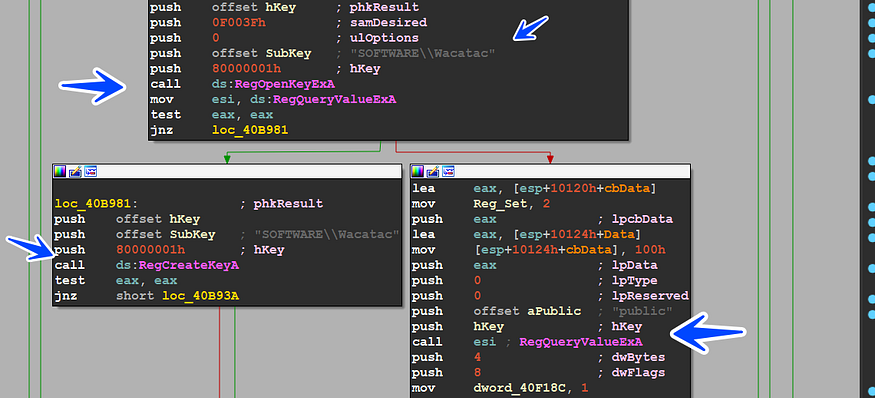
Registry Creations
the malware will do some registry operations and check if it’s run before or not, so it will try to open a key Called
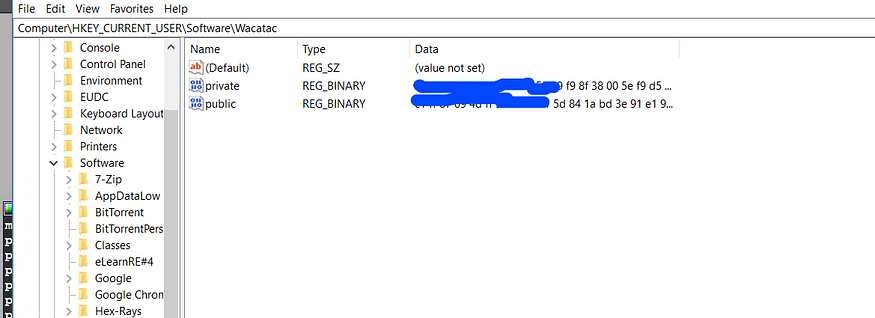
HKEY_CURRENT_USER\SOFTWARE\Wacatac
and if it failed it will create this key, but if it succeeded to open the key created before it will query some values related to encryption Keys saved in the registry key
COM Operations
then the malware tries to Create a COM instance by using CoCreateInstance() API
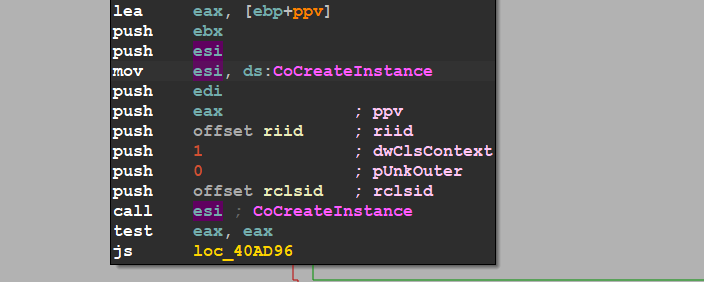
if the call successes there is a registry key created
HKEY_CLASSES_ROOT\CLSID\\{674b66998-ee92-11d0-ad71-00c04fd8fdff}
then the malware will use COM Capabilities for Deleting All shadow copies in the machine and using the “wql” WMI query language it’s like SQL and here it queries to retrieve all shadows copies in the machine
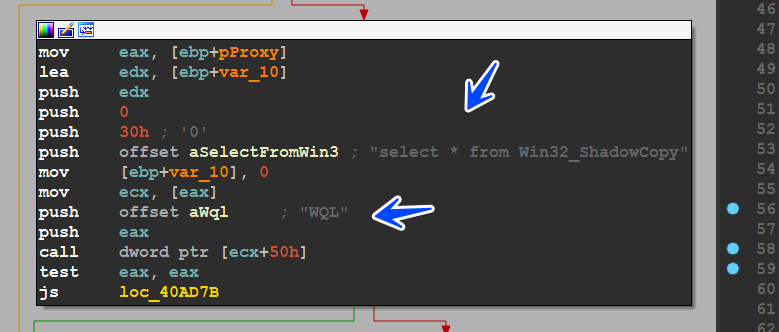
if you want to read more about shadow copies click here
Generating Keys
the specimen will generate a Public key and here I will talk in brief about the encryption method cause it is complex, this ransomware uses a combination of Curve25519 algorithm for the Elliptic Curve Diffie-Hellman (ECDH) key exchange scheme, Salsa20, RSA-2048, AES-256 ECB, and a simple block XOR algorithm to encrypt files and if you want more about encryption mechanism check this click here.
the malware saves the RSA-2048 Public Key in the registry
HKEY_CURRENT_USER\SOFTWARE\Wacatac\public
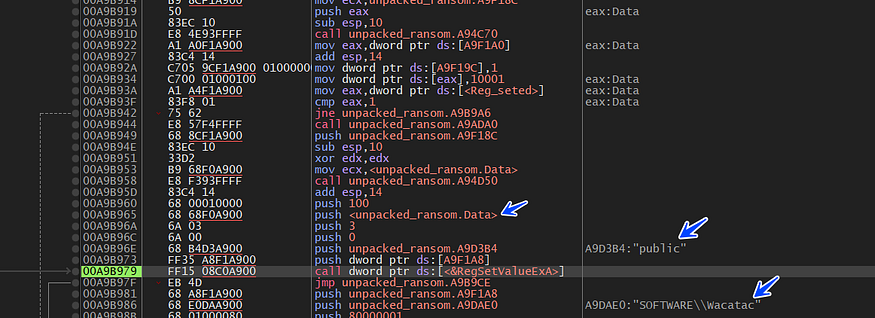
and also saves the private key in the same registry key under name of private
HKEY_CURRENT_USER\SOFTWARE\Wacatac\Private
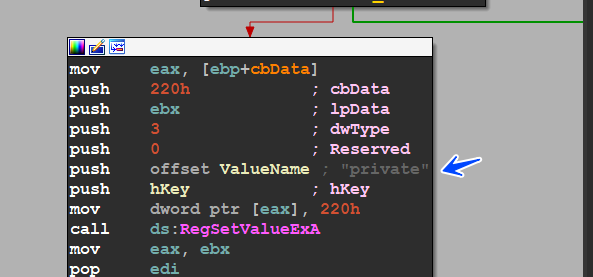
these keys are encrypted using SALSA20 Algorithm before it saved in the registry
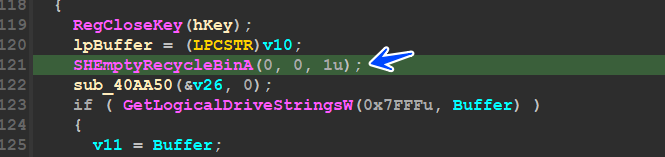
Delete all Files in Recycle Bin :
then the malware will start its ransom behavior by deleting all files in recycle bin using SHEmptyRecycleBinA() API
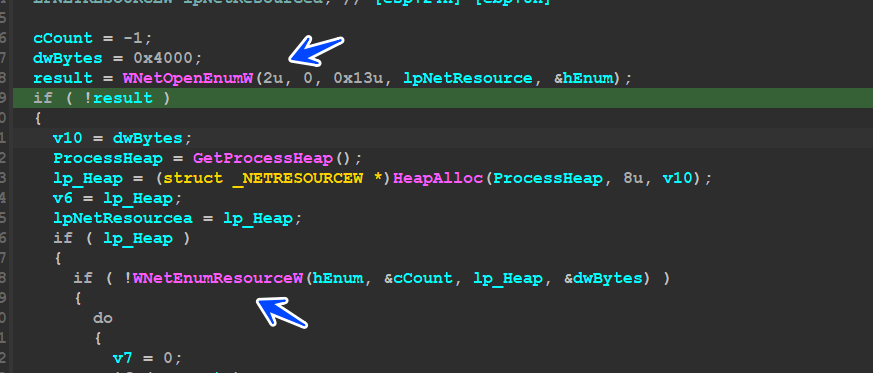
Get Network Files :
the malware starts by enumerating all Network Folders and will iterate over them until it gets a logical Folder and it does this by using
to retrieve all current directories and then encrypt them
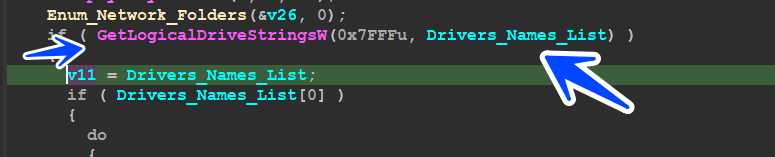
Ransom Behave :
the malware then will start to Get All Driver’s Names in the machine using
then the malware will start by dropping the readme File and encrypting the files
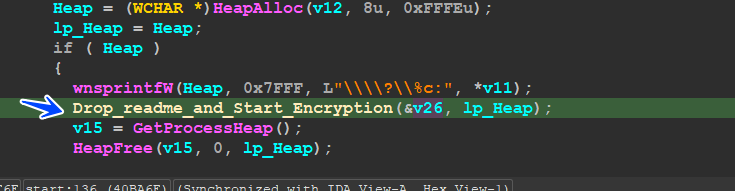
the malware will encrypt these Files and then drop readme in every directory,
the malware used QueueUserWorkItem() instead of normal calling and this API creates a thread only for this call this thread waits until another thread is done so tracing this behavior is harder but we will do it.
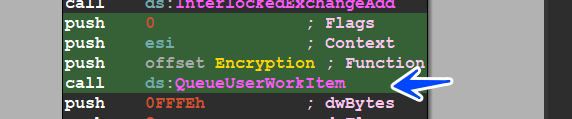
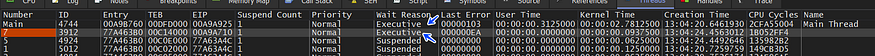
so let’s dig into this function and see how it’s done if we look at the debugger we will observe that there is 2 running thread after this call
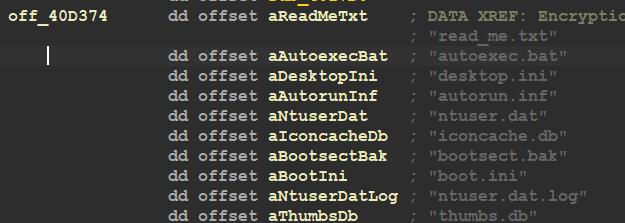
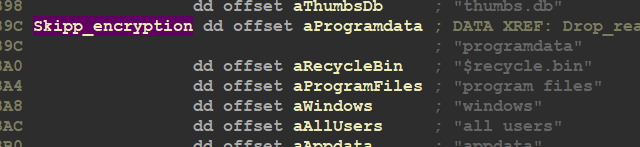
there are some Folders And Files the malware skips encrypting, these Files and Folders are related to the system and without it the system will crash and fail to boot correctly
FILES
Folders to Skip
the malware assigns a signature to the file before reading it
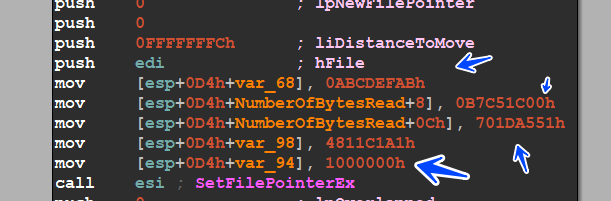
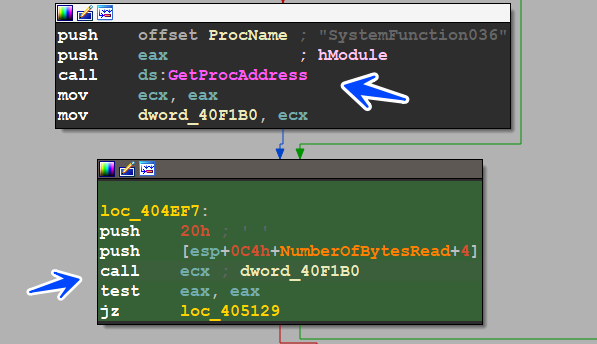
then the malware will call SystemFunction036() API which is used to generate random 32 bytes and these bytes is used for generating key
then the malware will start reading the content of the file using ReadFile() with 1000h bytes as the length of the allocated data

then the malware will encrypt the data using keys generated before
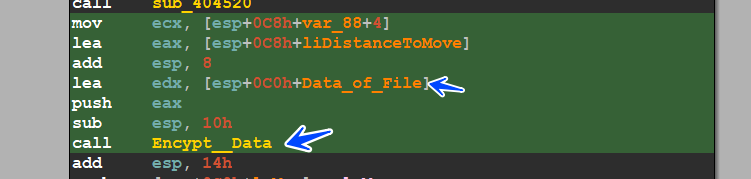
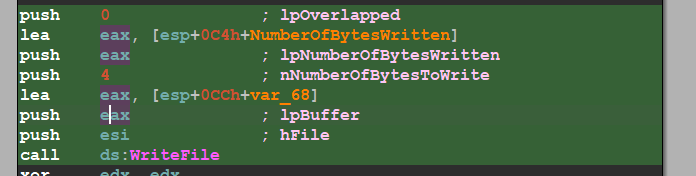
and then after encryption, it will write the data using
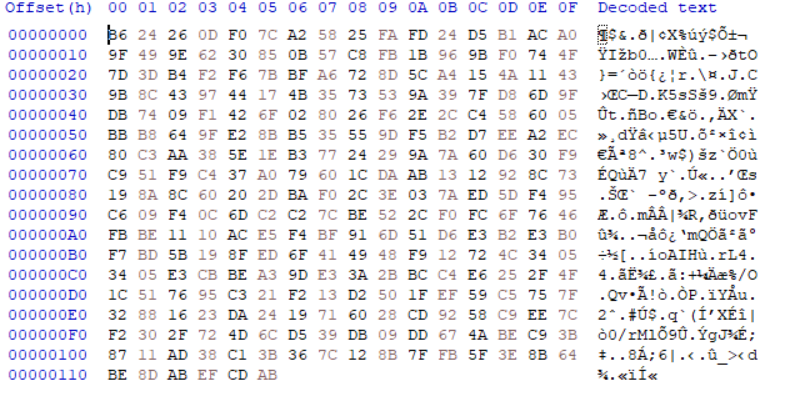
I will show you small pics in the debugger and how the data is encrypted, so I create a file containing this string “I was born in 1870”

and here is how the file looks like after encryption but I want to mention something that the encryption function append AES_Key and also something called File Maker,it appends them to the encrypted file content
Drop RansomNote :
the malware will resolve the ransom note and then drop it but write something in the note that you will never encrypt your Files without it, ya it’s the lock id and this lock id is the public key but encoded with base64

IOCs :
hash :
packed:
sha 256 : AB828F0E0555F88E3005387CB523F221A1933BBD7DB4F05902A1E5CC289E7BA4
unpacked:
sha 256 : 59E6D8CB209E6D46F74545EC551E3FE75D78A3FB7A26ECE220683AADAAE026A3
Downloaded File:
sha 256 : 0AB018C4C127A53EB70DEA8979AFA4A49ED66AE355E2515E6B79BFACDA65F5A6
Files :
ntos.database
Registry :
Computer\HKEY_CURRENT_USER\Software\Wacatac
Computer\HKEY_CURRENT_USER\Software\Wacatac\\Private
Computer\HKEY_CURRENT_USER\Software\Wacatac\\Public
HKEY_CLASSES_ROOT\CLSID\\{674b66998-ee92-11d0-ad71-00c04fd8fdff}
Network:
HTTP://iplogger[.]org/1Zqq77\ntos.database
Yara :
rule Death_Ransomware_Unpacked {
meta:
Discription = "yara about dececting unpacked version of Death Ransomware"
Author = "AzizMal"
Data = "4/4/2023"
contact = "@farghlyMal"
Strings:
$S1 ="expand 32-byte k"
$S2 ="https://iplogger.org/1Zqq77"
$S3 ="select * from Win32_ShadowCopy"
$S4 ="Win32_ShadowCopy.ID='%s"
$S5 ={B? 19 04 00 00 0F B7 C0 8? ?? ?? ?? 66 3B ?? [4-6] B? 3F 04 00 00
66 3B C1 [4-6] B? 23 04 00 00 8? ?? ?? ?? 66 3B ?? [4-6] B? 22 04 00 00
8? ?? ?? ?? 66 3B ?? [4-6]}
condition:
uint16(0) == 0x5A4D and all of them
}
TTPS:
Network Share Discovery (T1135)
File and Directory Discovery(T1083)
Native API execution(T1106)
Data Encrypted (T1486)
Ransomware (T1486.001)
