Death Ransomware Analysis_part1
Introduction
Hello Cyber Geeks, today I am going to explain how Death Ransom behavior is done and how the encryption method happens, and how to detect it using Yara and IOCs
overview :
Discovered by GrujaRS, DeathRansom is malicious software, classified as ransomware. In general, systems infected with malware of this type have their data encrypted. The cybercriminals behind the encryption then demand a ransom to be paid for decryption tools/software, there are 2 versions of Death Ransom, and one of them does not encrypt your Files it just appends “.wctc” extension to the Fils, for example,
lol.jpg → lol.jpg.wctc , but the data is the same data with no encryption, let’s dig into the code and properties of the File, the other one encrypts it without appending any extensions.
sha 1: 65B5F8CC7B0B6315FE934578F9CAD4FAF7DA41F2
First Stage :
the malware comes in a packed formal and many noisy mangled symbols generated by the C++ Compiler, so let’s try to unpack it using some methods and techniques
so there are some suspicious calls that the malware uses to allocate memory and then unpack the code in this memory like
we need to search for these APIs in The imports section in the Malware and trace these calls and look at what happens in the allocated spaces may we get the 2Stage or another shell Code,
I see a suspicious call to LocalAlloc() which is used to allocate a local memory space and the uBytes Globale Variable is used in another place which is a big indicator of the unpacking process
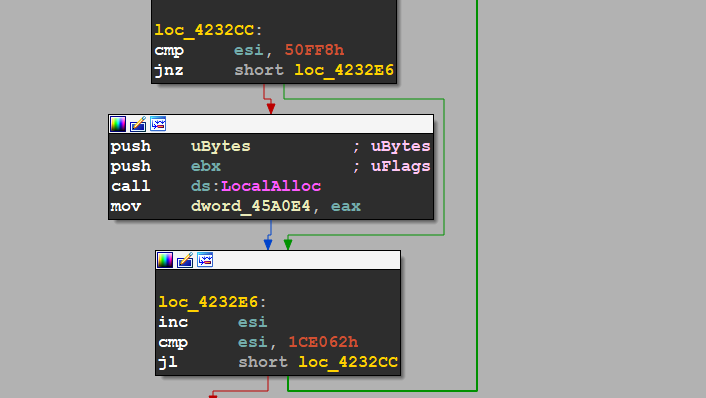
and we see another call to GetProcAddress() which is used to get the address of an API, so we will complete the analysis using the debugger and appending some breakpoints in the APIs mentioned above
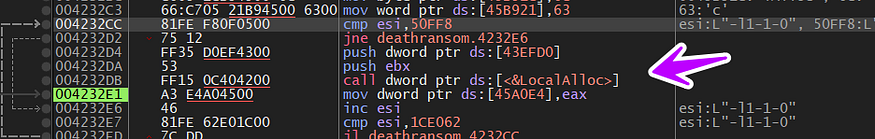
here is our debugger hitting the first breakpoint in calling LocalAlloc, I will dump the address of the memory allocated and complete running our debugger
we hit another call to GetPorcaddress resolving the address of VirualProtect which is used in changing the protection of a memory space
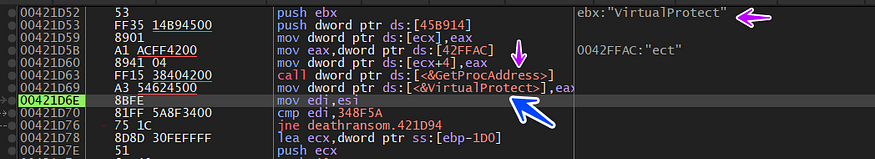
and if we take another look at the memory allocated we will see that it’s filled with some bytes which the debugger will transfer the execution to this ShellCode
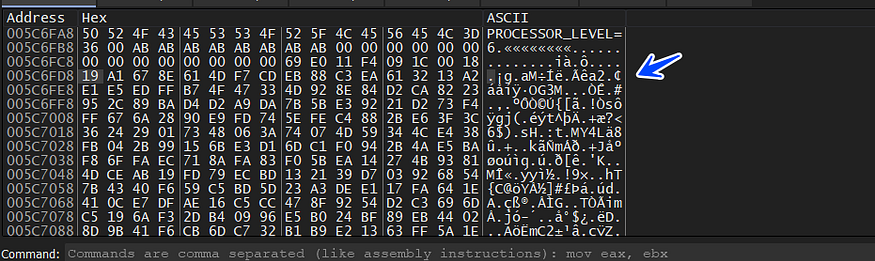
and here is how the program starts executing the shellcode
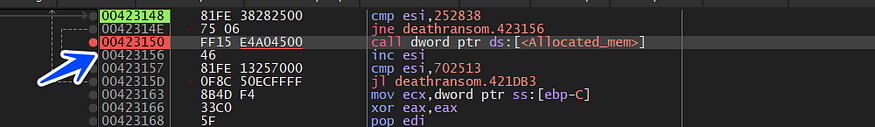
we will set a memory breakpoint on the execution of this memory, and here is the hit of the breakpoint
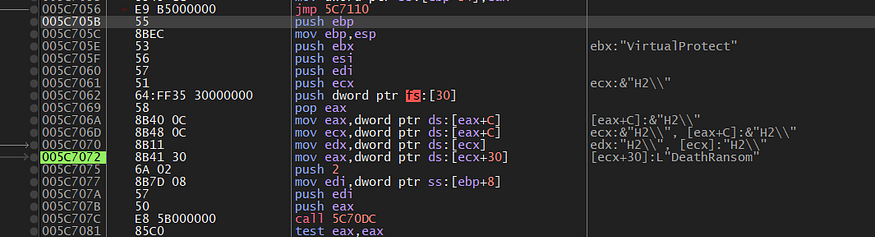
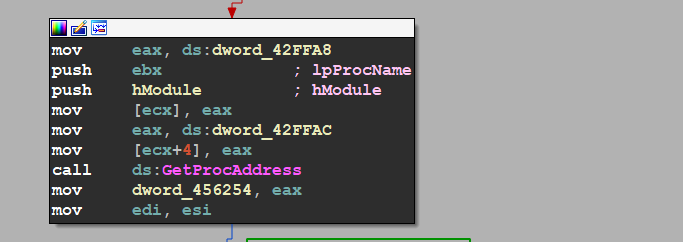
so we will complete the breakpoint set before, and we will hit a call to virtualAlloc() API which is used in allocating a memory space
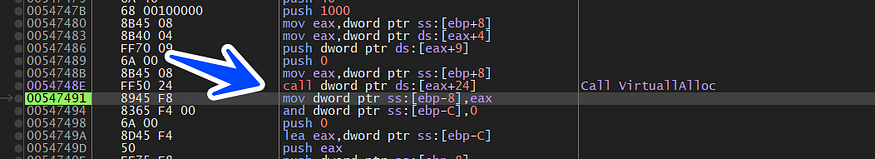
and I will dump the address of the memory and see what the malware will do in this space ,,, the program is writing another shellcode that we will trace again
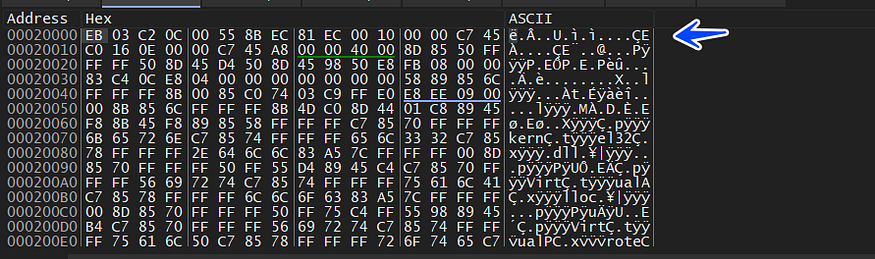
and here is how another transfer execution is done to this shellcode
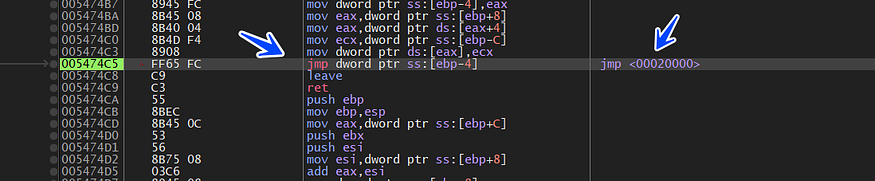
we hit another virtualAlloc(), I dump the address allocated by this call
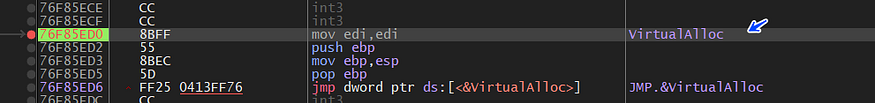
let’s complete the unpacking process
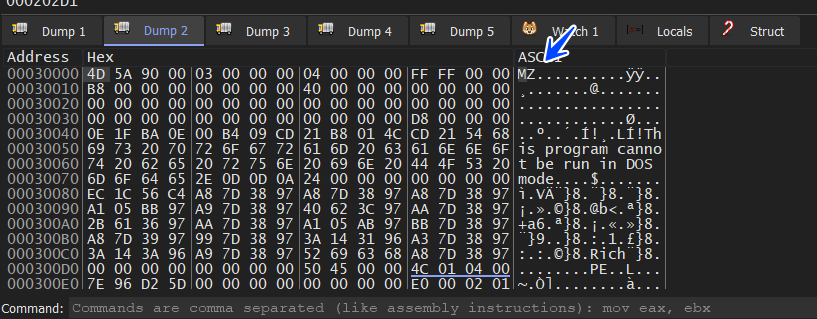
WOW, we get an MZ Header, and here is the unpacking process ended, the program will transfer the flow to the start of the code section but I will dump this PE File and run it throw the analyzing process(static and dynamic)
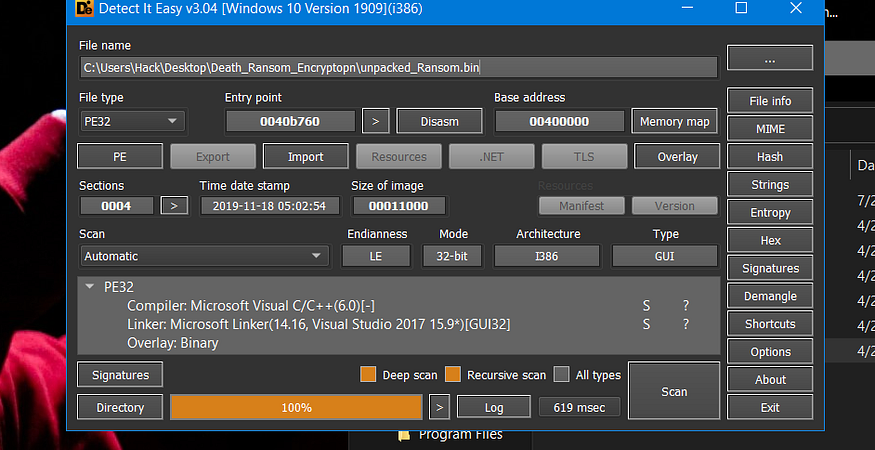
so the sample is not packed and this is the real ransomware
I will complete the full analysis in the next part, wait for it
my part 2 about technical analysis
thanks for reading……..
